Check for default and weak credentials across all hosts in your workspace instantly!
Features
- Check for default and weak credentials in a target environment.
- Single & built-in multi target selections.
- Customized wordlist selections for usernames and passwords.
- Automatic brute forcing of all services via BruteX.
- Reporting of all output via the Command Execution Add-on.
Usage
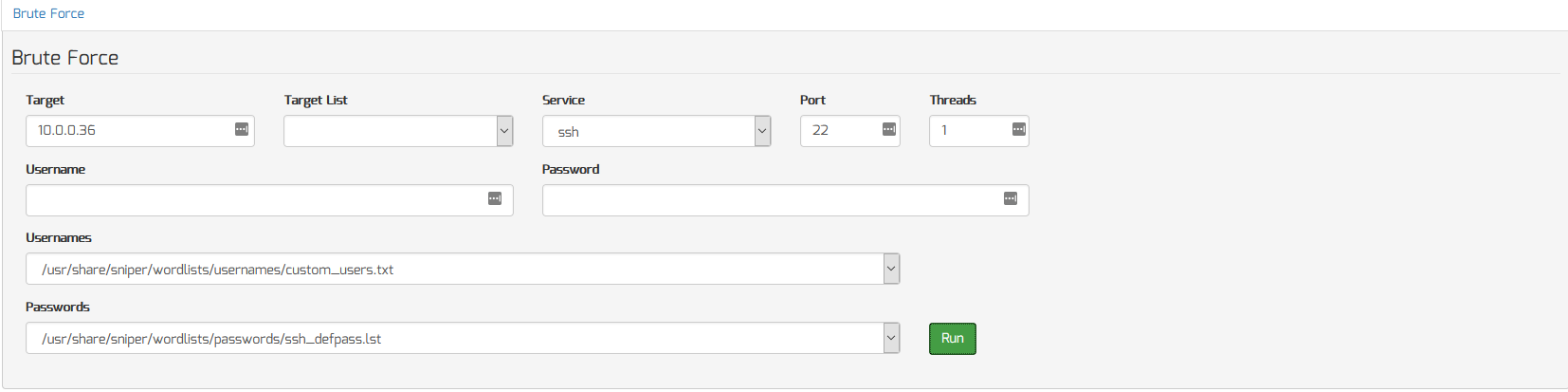
Brute Force A Single Service On A Single Target
To brute force a single service on a single target, do the following:
- Click on any workspace from the Workspace Navigator
- Scroll down and click “Brute Force” menu to access the Brute Force Add-on
- Enter the taget’s IP/hostname/domain in the “Target” input box
- Select the service you want to brute force (ie. ssh, etc.) from the “Service” menu
- Enter the port number (ie. “22” for standard SSH) in the “Port” input box
- To check for a specific username or password, enter them in the “Username” and “Password” input boxes
- To use a list of usernames and passwords, select a wordlist for both the “Usernames” and “Passwords” menu items
- Click the “Run” button to begin the scan
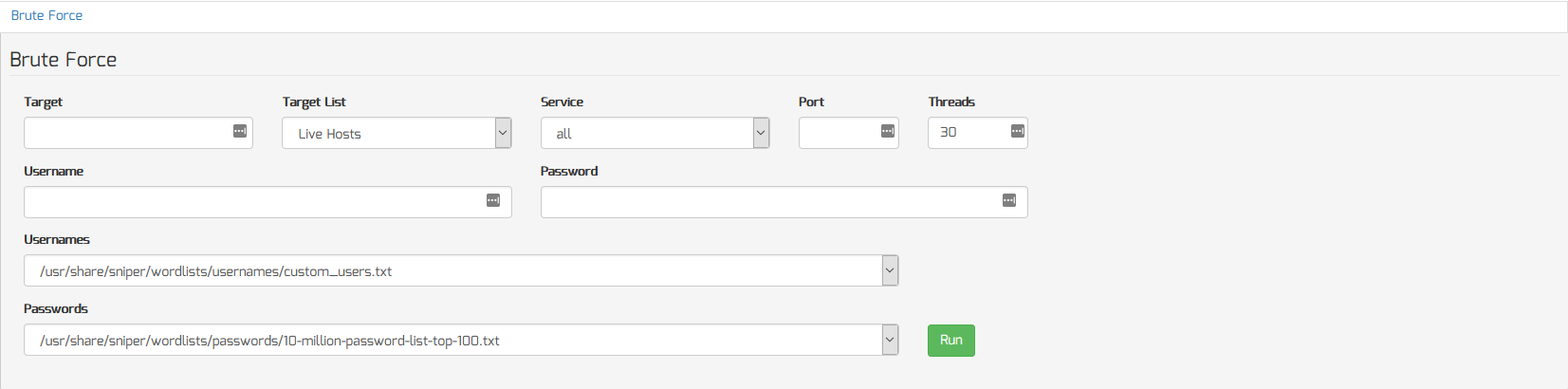
Brute Force All Open Services On ALL Live Hosts
To brute force all open services on ALL live hosts, do the following:
- Click on any workspace from the Workspace Navigator
- Scroll down and click “Brute Force” menu to access the Brute Force Add-on
- Select “Live Hosts” from the “Target List” menu
- Select “all” from the “Service” menu
- Click the “Run” button to begin the scan
This assumes you have already scanned your workspace for live hosts which will automatically populate your “Live Hosts” target list.