Automatically fuzz for OWASP TOP 10 vulnerabilities and discover hidden content easily with the new Sn1per Professional Fuzzer Add-on!
Features
- Automatically fuzz dynamic URL’s for OWASP TOP 10 vulnerabilities.
- Discover hidden content in a target environment.
- Spider all URL’s within a target environment.
- Single & built-in multi target selections.
- Customized wordlist selections and options via the GUI.
- HTML and text based reports for all tools (ie. Black Widow, InjectX, SQLMap, Arachni, FFuf, Dirsearch, Gobuster)
- Reporting of all output via the Command Execution Add-on.
Adding Custom Wordlists
To add custom wordlists, add any .txt files to the following directory:
/usr/share/sniper/wordlists/custom/*.txt
Usage
Discover Hidden Content
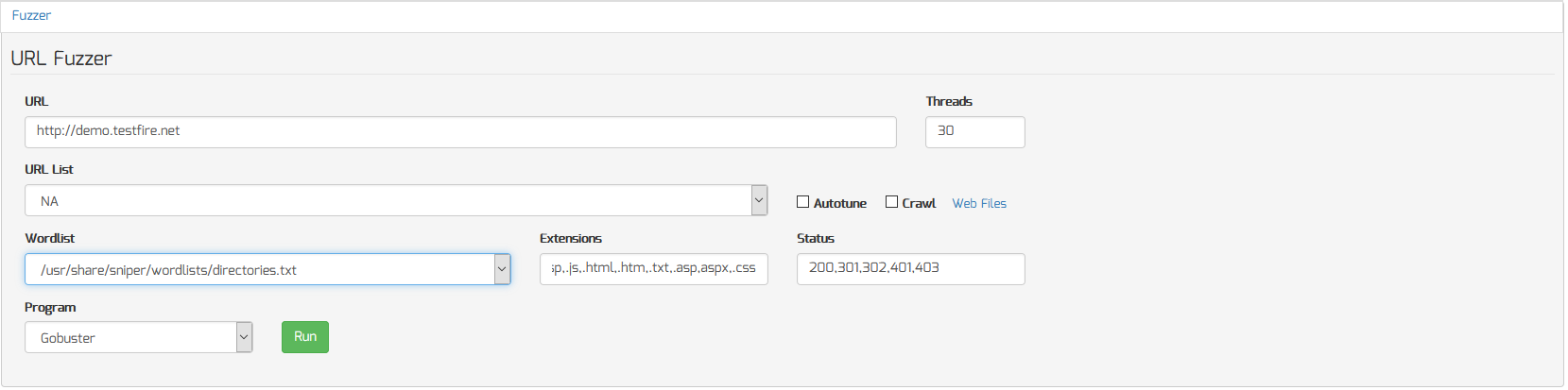
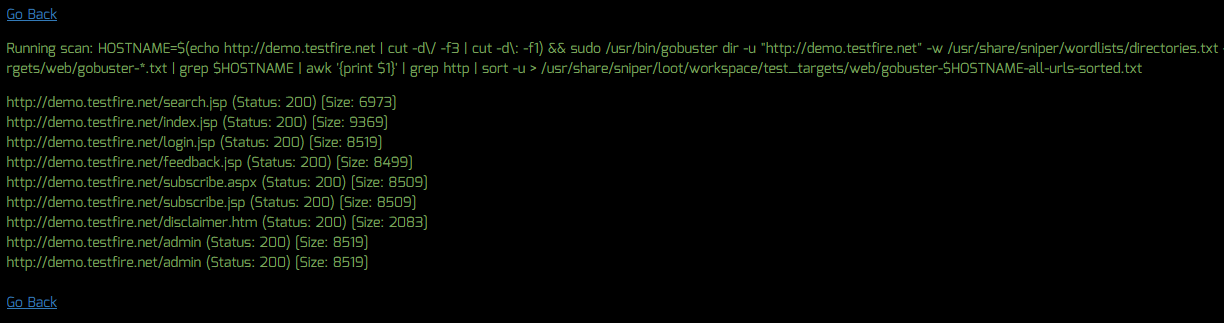
To fuzz a specific URL to discover hidden files and folders, do the following:
- Click on any workspace from the Workspace Navigator
- Scroll down and click “Fuzzer” menu to access the Fuzzer Add-on
- Enter the starting URL you want to brute force in the URL field
- Select a wordlist to use from the “Wordlist” menu
- Select a program to use (ie. Gobuster, Dirsearch, Ffuf)
- Click the “Run” button to begin the scan
Crawl/Spider All URL’s
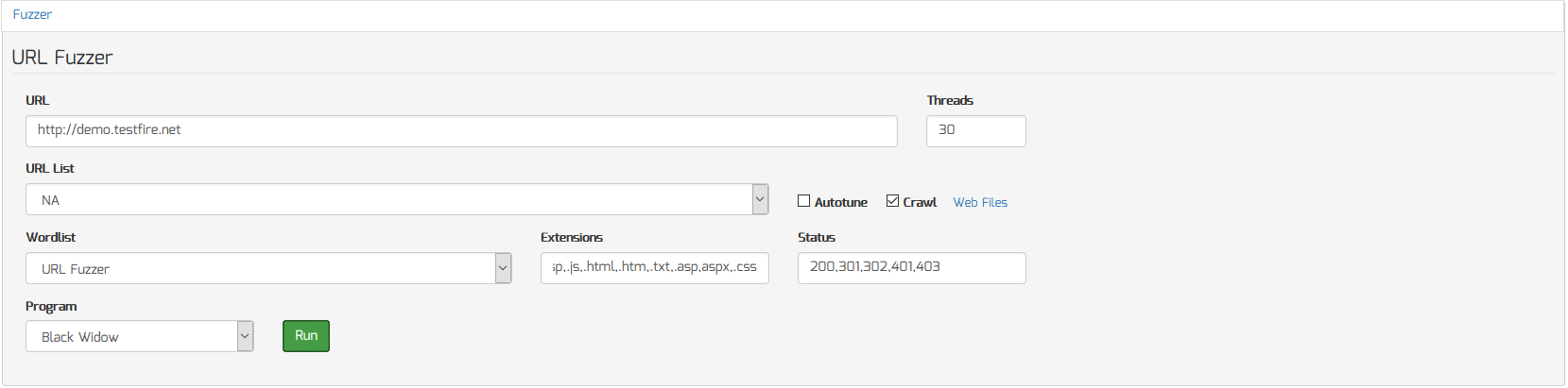
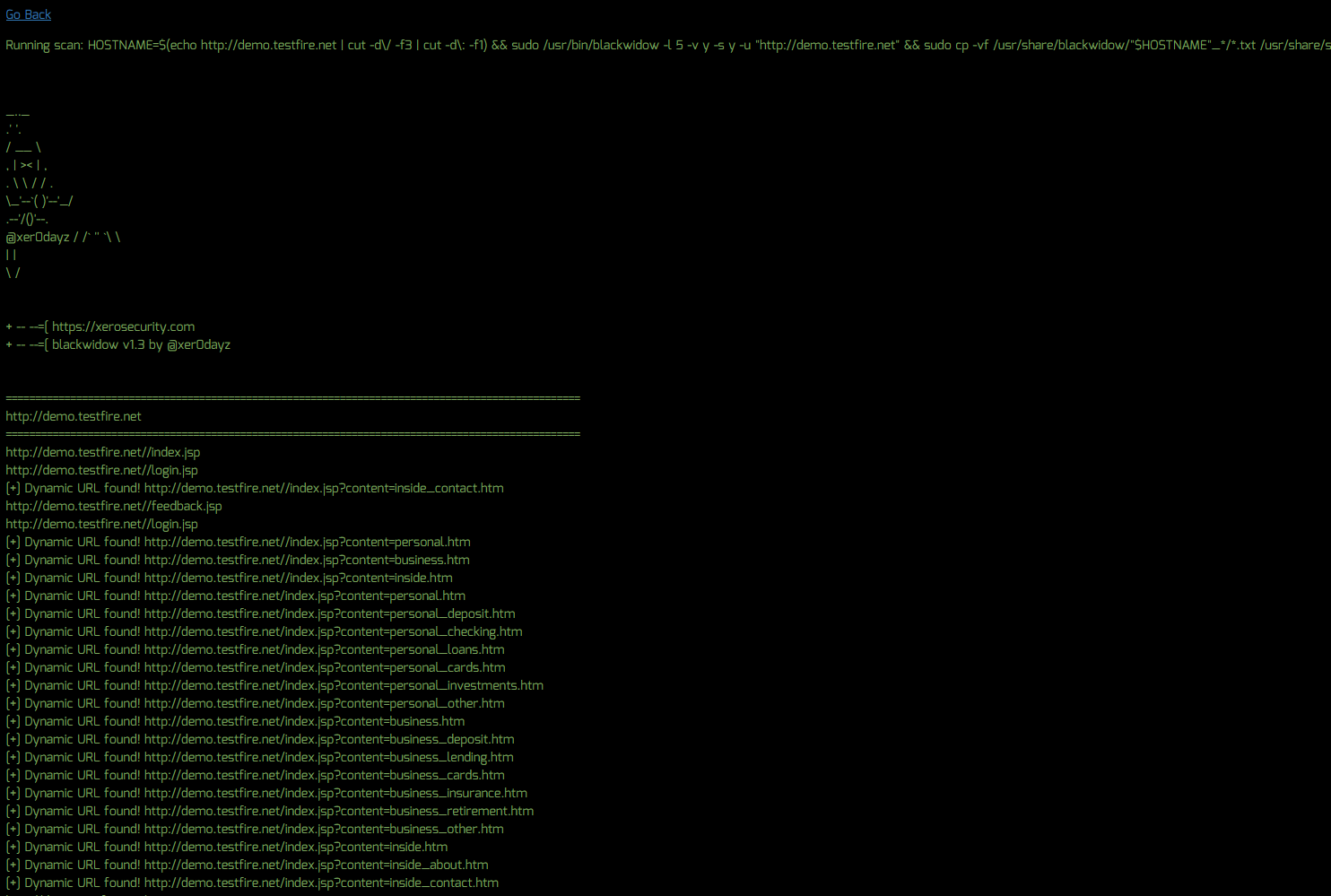
To crawl/spider a website to discover all URL’s, do the following:
- Click on any workspace from the Workspace Navigator
- Scroll down and click “Fuzzer” menu to access the Fuzzer Add-on
- Enter the starting URL you want to spider in the URL field
- Select “BlackWidow” from the “Program” menu
- Click the “Run” button to begin the scan
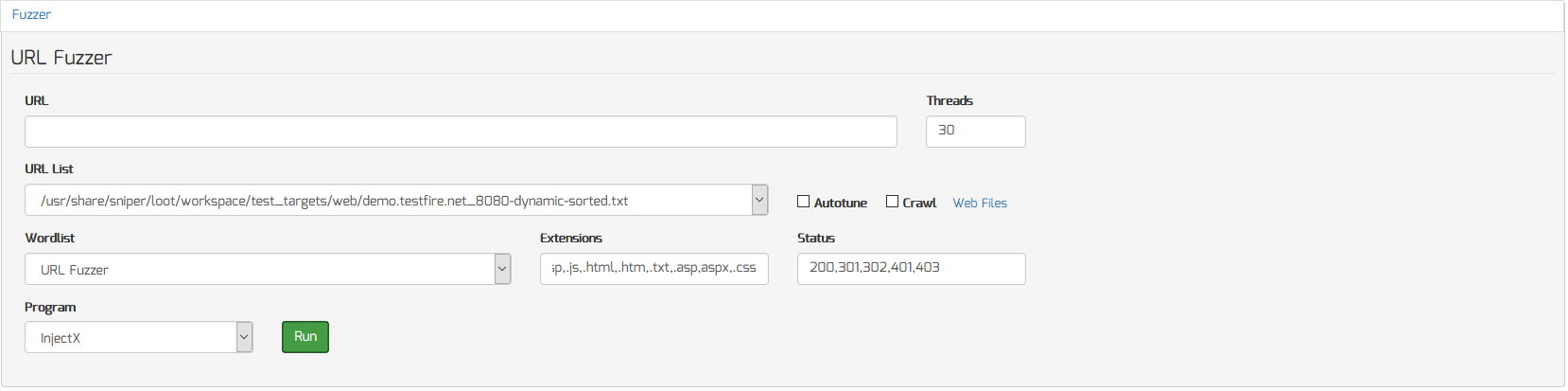
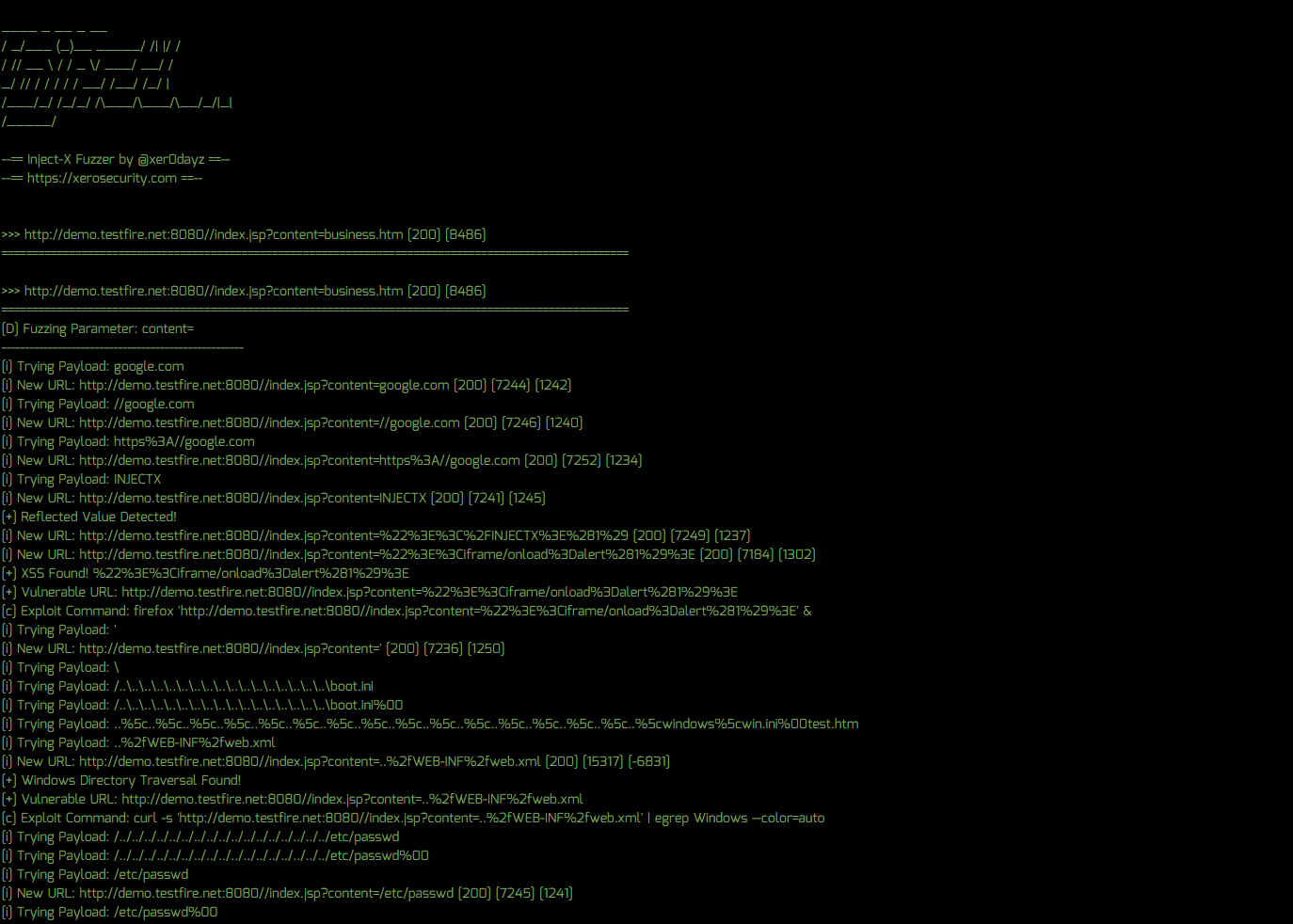
Fuzz All Dynamic URL’s for OWASP Top 10 Vulnerabilities
To fuzz all dynamic URL’s for OWASP Top 10 vulnerabilities, do the following:
- Click on any workspace from the Workspace Navigator
- Scroll down and click “Fuzzer” menu to access the Fuzzer Add-on
- Select a URL list to fuzz from the “URL List” menu (ie. target.com_port-dynamic-sorted.txt)
- Select “InjectX” from the “Program” menu
- Click the “Run” button to begin the scan
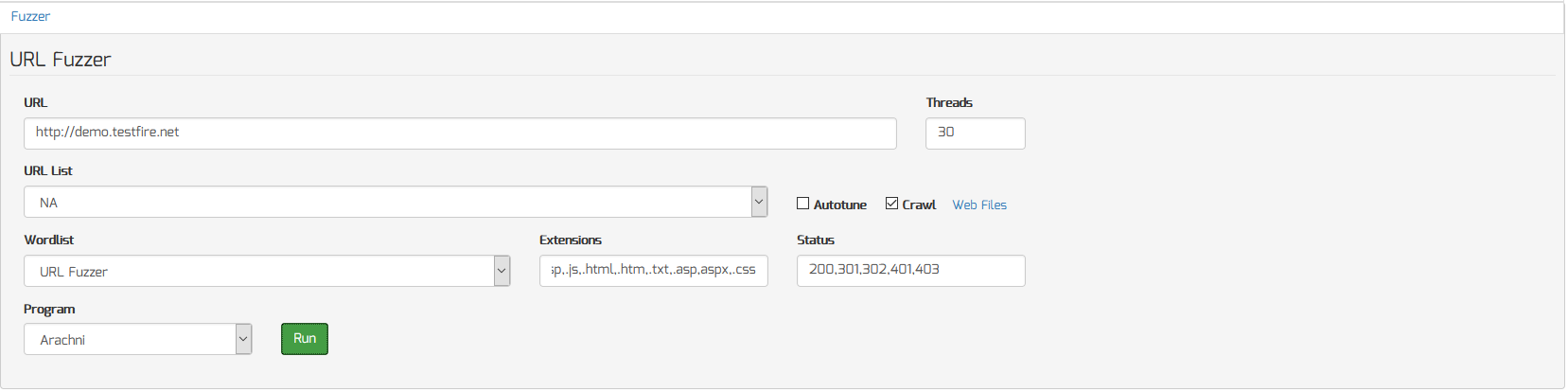
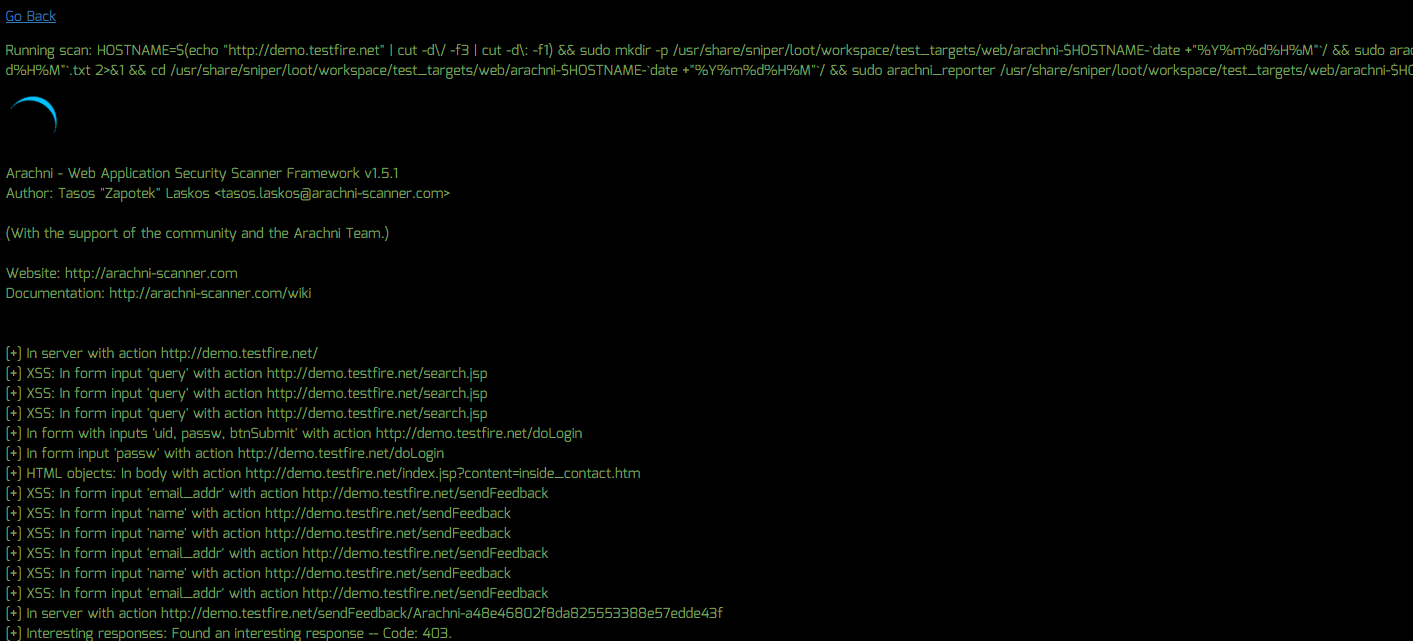
Run Automated Web Application Scans
To run automated web application scans against a target website, do the following:
- Click on any workspace from the Workspace Navigator
- Scroll down and click “Fuzzer” menu to access the Fuzzer Add-on
- Enter the starting URL you want to spider in the URL field
- Select “Nikto”, “Arachni” or “SQLMap” from the “Program” menu
- Click the “Crawl” checkbox to spider all URL’s
- Click the “Run” button to begin the scan
Misc Usage Notes
When using the Fuzzer Add-on, it’s important to keep the following in mind:
- Only the URL field OR the URL List field can be selected at one time. If URL List does not equal “NA”, the URL List will be used by default.
- To fuzz all web hosts in a workspace, you can select the ‘webhosts-sorted.txt’ file in the URL List drop down menu.
- To specify extensions to scan for, use ext, ext2, ext3 for Gobuster and Dirsearch. For FFuf, use .ext, .ext2, .ext3
- The “Autotune” option only applies to Gobuster and FFuf. This will auto filter results based on heuristics.
- The “Crawl” option only applies to both SQLMap and Arachni to increase the crawl/spider limits.
- All output from all tools is stored under /usr/share/sniper/loot/workspace/<WORKSPACE>/web/. There is also a link within the fuzzer addon for convenience.
- HTML reports are produced for both Arachni and FFuf scans.
- Use the built-in URL Lists to automatically select URL lists based on previous scans. You can also add .txt files to your /usr/share/sniper/loot/workspace/<WORKSPACE>/web/ directory to automatically import them.
- You can also use the “FUZZ” keyword in the URL field when using FFuf to select a specific location to begin fuzzing (ie. https://target.com/url.php?file=FUZZ).