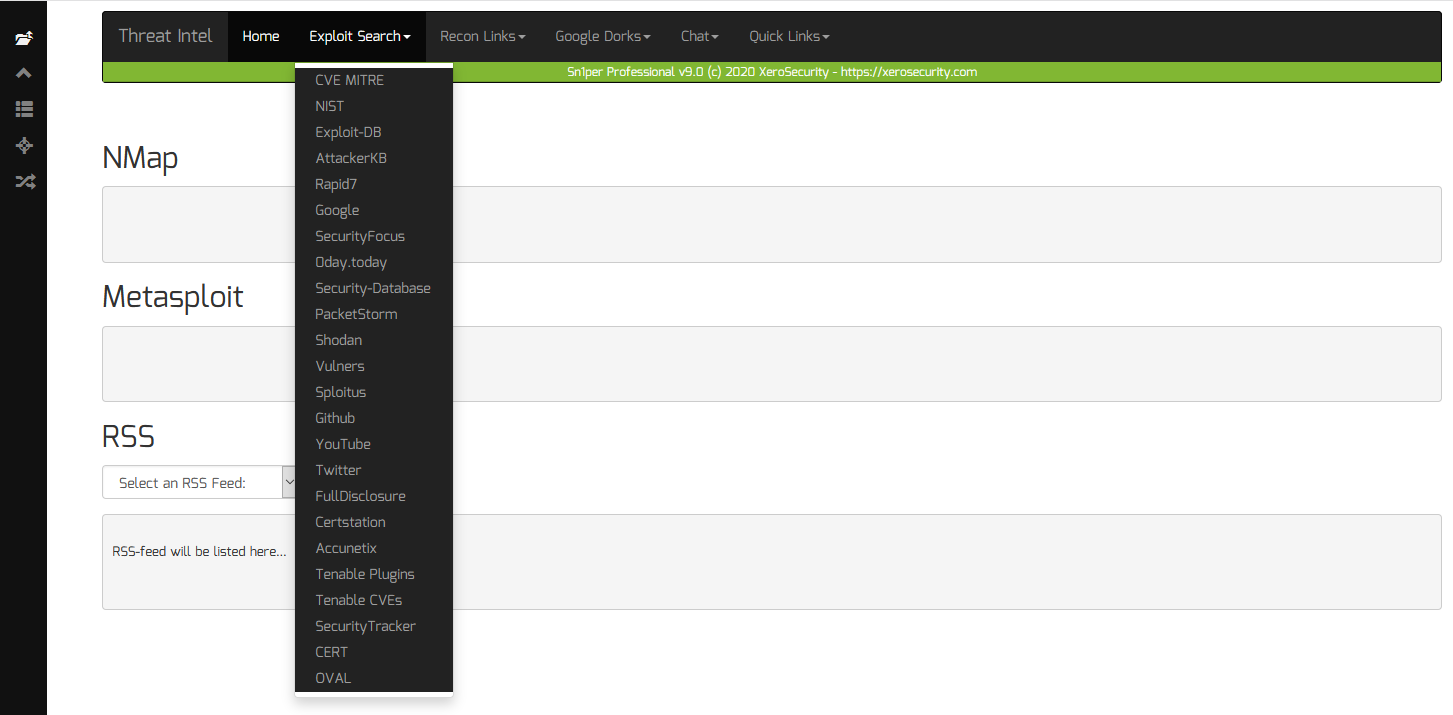
Stay up-to-date with the latest emerging security threats, vulnerabilities, data breaches and exploit releases with the new Threat Intel Add-on for Sn1per Professional!
Features
- Quickly search for the latest CVE’s, exploits and vulnerabilities easily
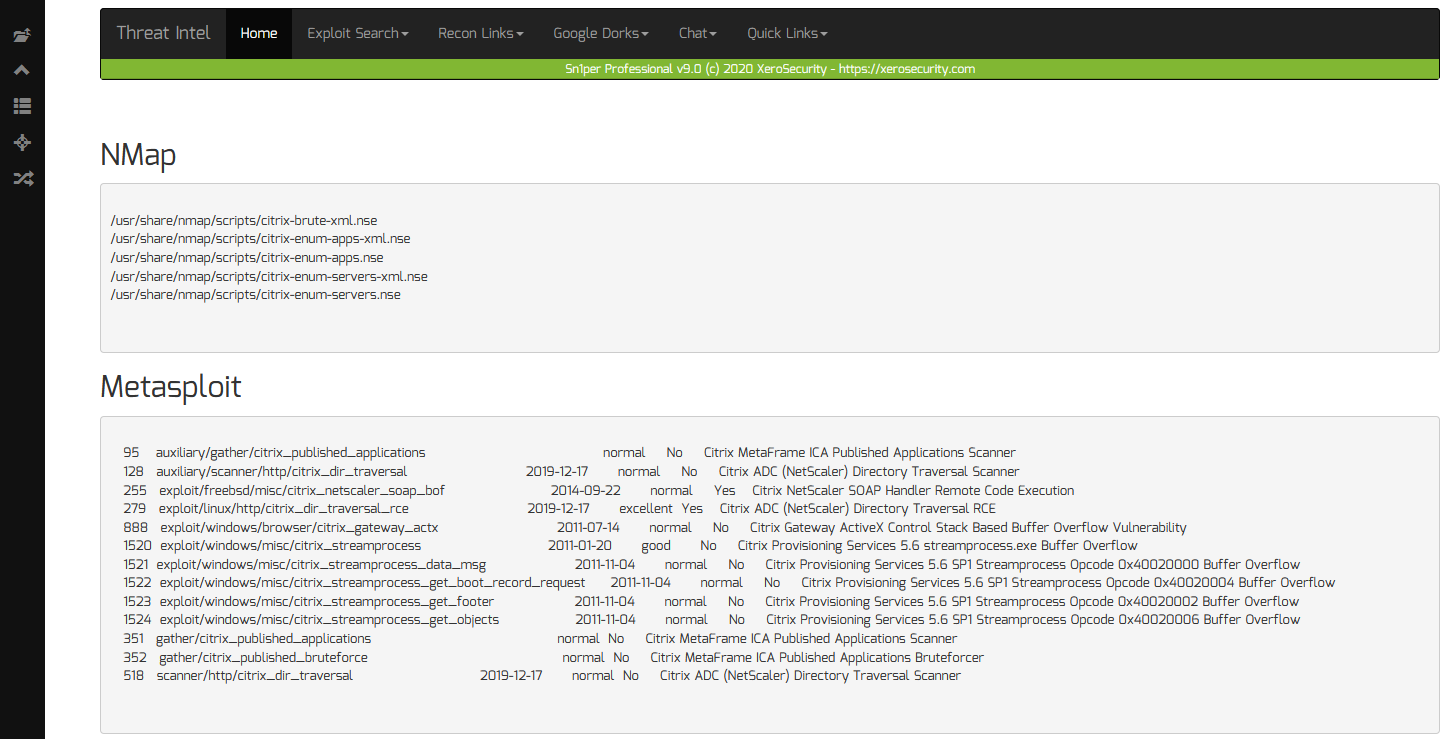
- Search local NMap scripts and Metasploit modules easily
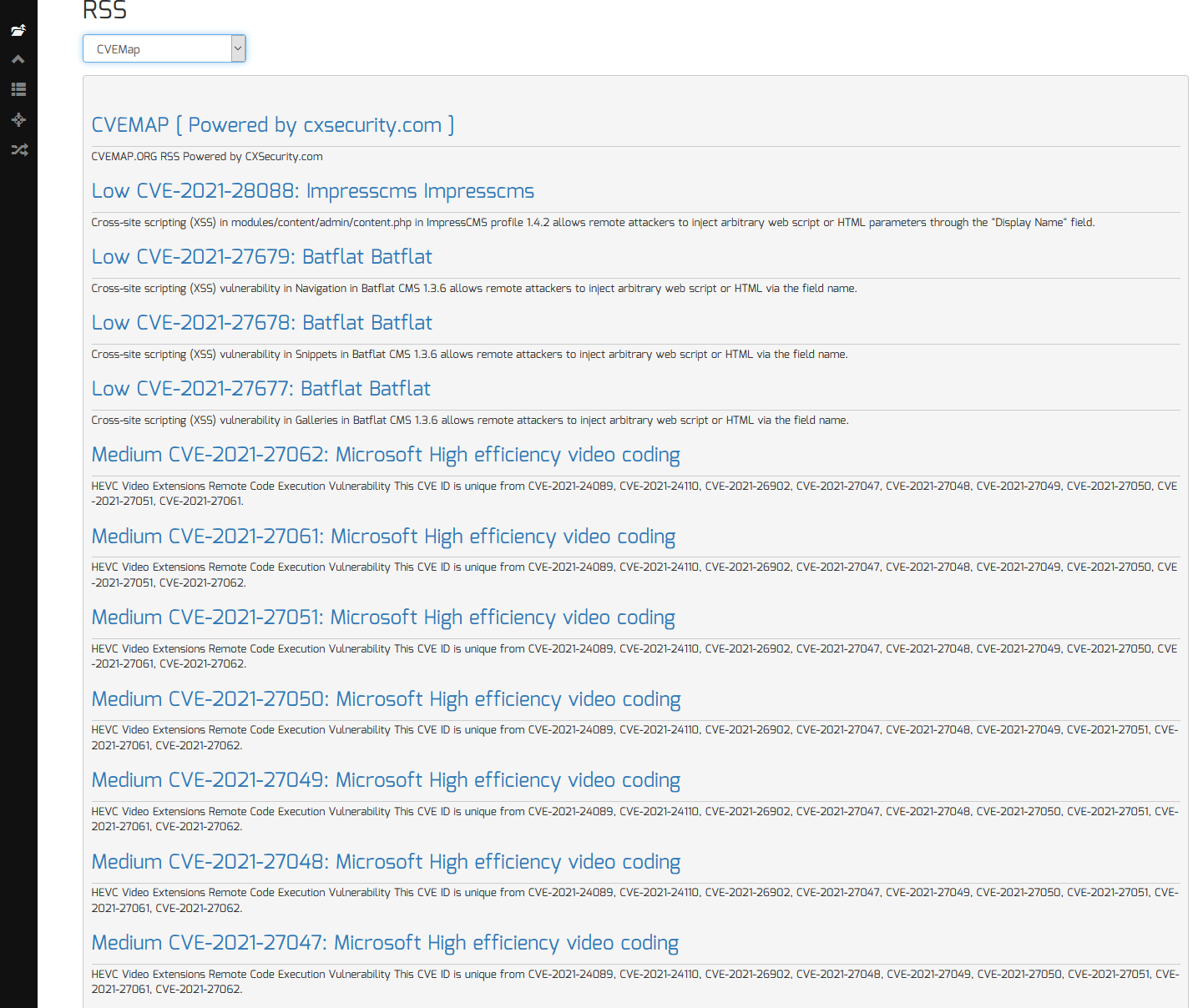
- Stay up-to-date on emerging threats, vulnerabilities, news and exploits with over 20+ hand picked RSS feeds
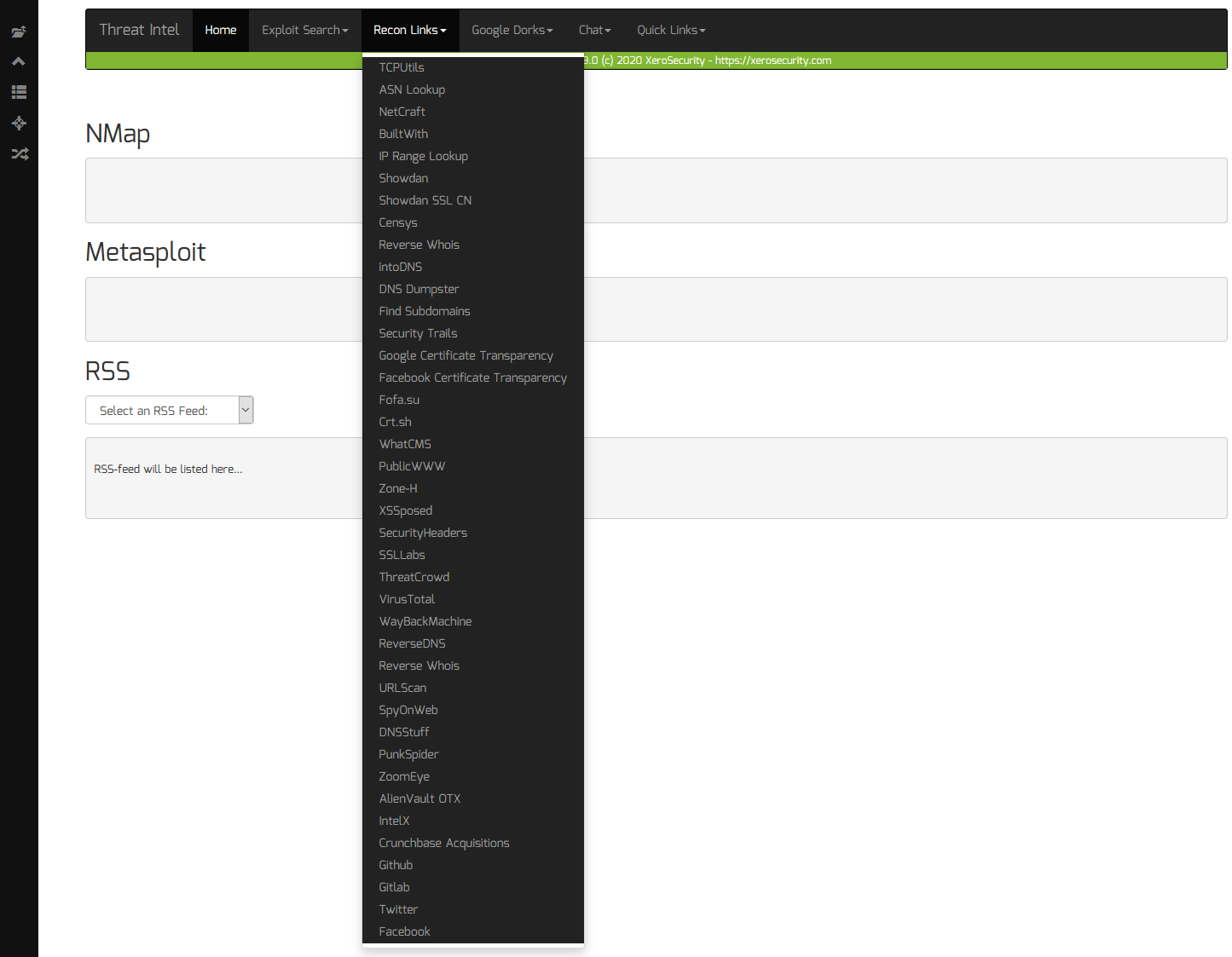
- Perform OSINT and reconnaissance on any target IP or domain name, using built-in recon and Google dork links
- Join the top security servers on Slack and Discord to gather and share community based intelligence
Usage
Search for NMap or Metasploit Exploits
To search for NMap or Metasploit scripts and exploits, do the following:
- Click on any workspace from the Workspace Navigator
- Scroll down and click “Threat Intel” menu to access the Threat Intel Add-on
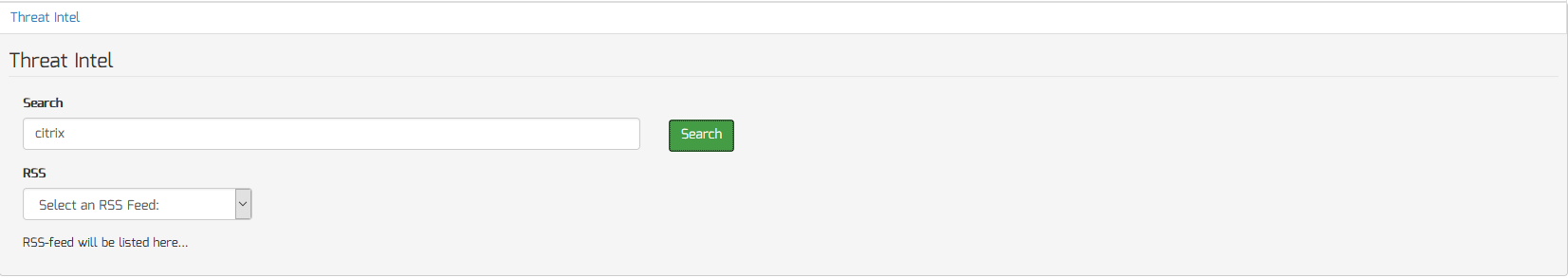
- Enter a keyword to search for in the “Search” input box (ie. citrix)
- Click the “Search” button to start the search
Viewing Threat Intel RSS Feeds
To view the latest threat intel rss feeds, do the following:
- Click on any workspace from the Workspace Navigator
- Scroll down and click “Threat Intel” menu to access the Threat Intel Add-on
- Select any of the RSS feeds from the “RSS” menu
Perform Recon Using 3rd Party Online Tools
To perform recon against a domain name, company or IP address, do the following:
- Click on any workspace from the Workspace Navigator
- Scroll down and click “Threat Intel” menu to access the Threat Intel Add-on
- Enter the keyword to search for in the “Search” input box (ie. hackerone.com)
- Click on any of the recon or Google dork links from the “Recon Links” and “Google Dorks” menus
Searching For Exploits and CVE’s Using 3rd Party Online Tools
To search for exploits and CVE’s using 3rd party online tools, do the following:
- Click on any workspace from the Workspace Navigator
- Scroll down and click “Threat Intel” menu to access the Threat Intel Add-on
- Enter the keyword to search for in the “Search” input box (ie. proxylogon)
- Click on any of the exploit links from the “Exploit Links” menu