Attack Surface Management With Sn1per Professional
External Attack Surface Management (EASM) has become a crucial function for every organization to gain visibility of their perimeter security. Having the right tools and processes in place is vital to detecting new vulnerabilities before attackers do. In this blog post, we will outline the basic steps for discovering the attack surface with Sn1per Professional.
Discover the External Attack Surface
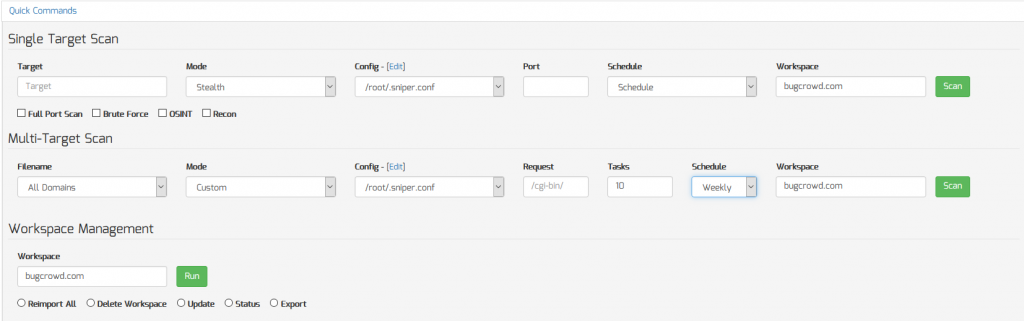
Discovering the attack surface with Sn1per Professional is easy. Simply enter the target domain name into the “Quick Commands” sections of the Command Execution Add-on v2.0 for Sn1per Professional and enable the “Recon” option to gather all sub-domains. Set a daily, weekly or monthly scan schedule to continuously scan the attack surface.
Asset Inventory Management
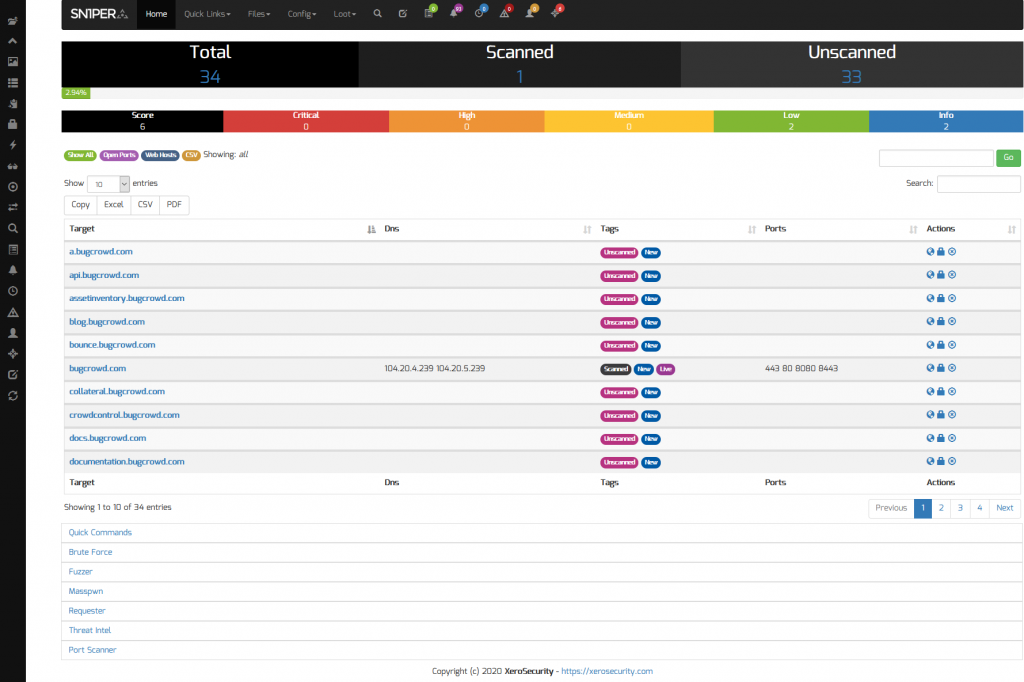
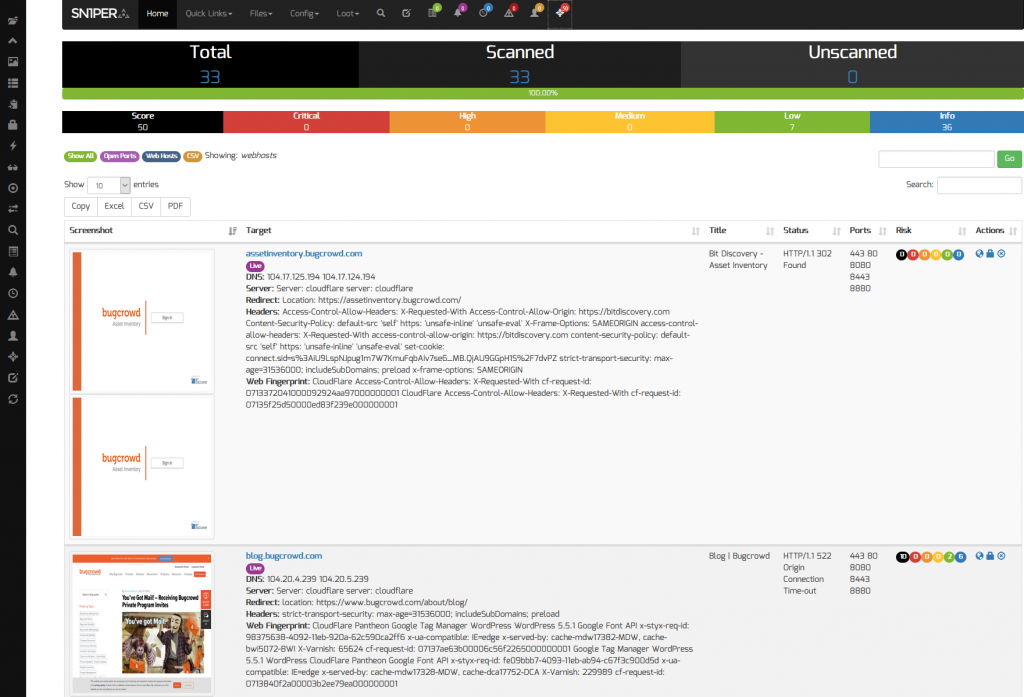
Sn1per Professional makes it easy to view the entire asset inventory or any target domain by clicking on the target workspace from the Workspace Navigator. This allows organizations to view all of their external facing assets and routinely scan for changes.
Visibility and Risk Reduction
Sn1per Professional provides an up-to-date view of your attack surface and provides an overall workspace vulnerability matrix and individual asset risk scores to find, prioritize and secure your entire attack surface. This is done by selecting the “All Domains” option from the “Multi-Target” drop down menu included with the Command Execution Add-on v2.0 and clicking the “Scan” button.
Notifications and Change Auditing
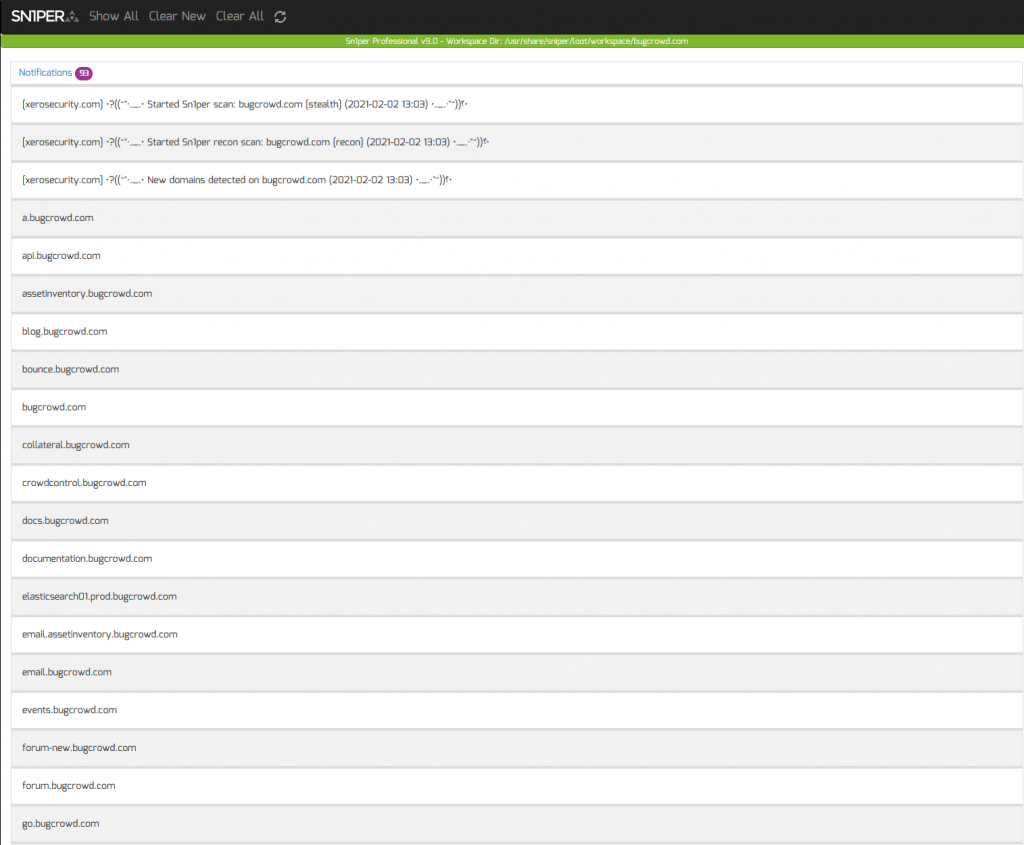
Having a time-stamped log of key changes is vitally important when monitoring the attack surface. Sn1per Professional makes this easy by letting you view the following notifications and changes directly from the UI without the need for external services such as e-mail, Slack or Discord:
- New domains discovered
- New URL’s discovered or changed
- Host status changes
- Host port changes
- Vulnerabilities discovered
- Scan status changes (ie. start/finish)
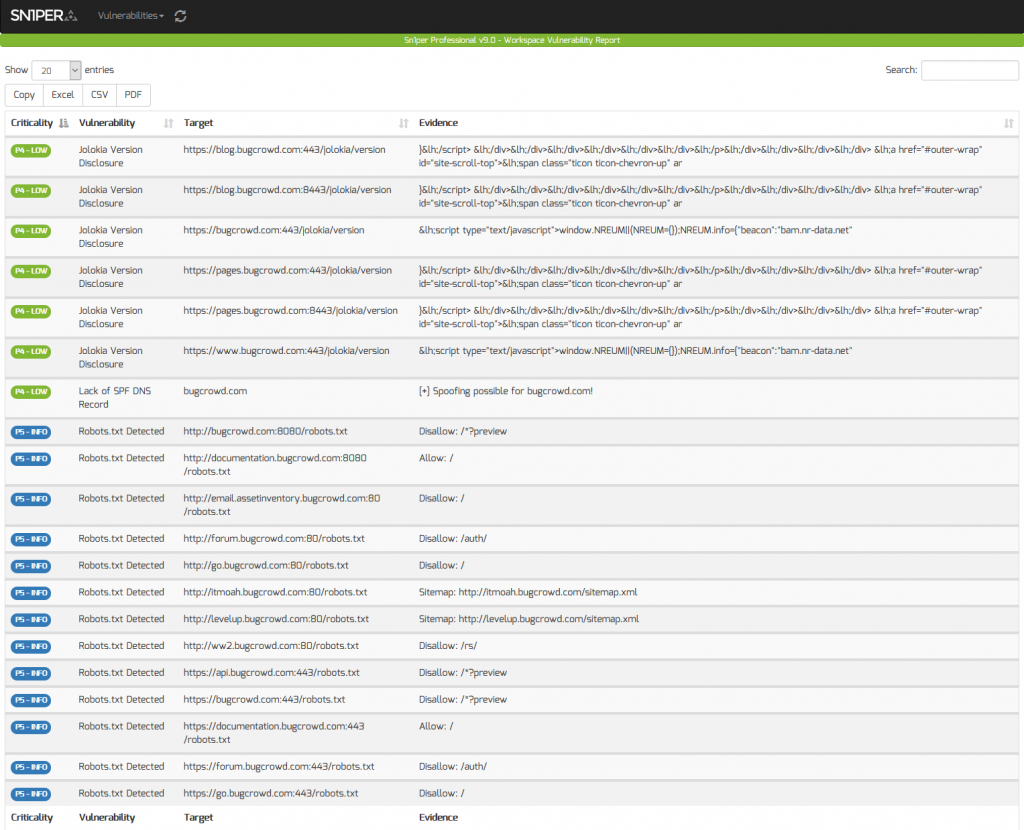
Threat and Vulnerability Management
Scanning for the latest vulnerabilities and CVE’s is critical for any Attack Surface Management (ASM) service or software. With Sn1per Professional, it’s easy to scan for the latest vulnerabilities and generate PDF, CSV, TXT or XLS vulnerability reports. Quickly sort and filter by criticality, vulnerability name, target or evidence to quickly find the data you’re looking for.
More Info
This blog post outlines the basic steps to discover the attack surface using Sn1per Professional. To find out how Sn1per Professional can help you or your organization perform Attack Surface Management, check our latest demo video and blog post here. If you’re looking for a free and open source option to perform attack surface monitoring, try our Sn1per Community Edition.
Get Your Copy Today!