CVE-2024-21733 Apache Tomcat HTTP Request Smuggling
Our security research team recently discovered a critical “0day” vulnerability which was assigned CVE-2024-21733. The vulnerability was discovered by xer0dayz from Sn1perSecurity LLC and allows attackers to force a victim’s browser to de-synchronize its connection with websites hosted on top of Apache Tomcat, causing sensitive data to be smuggled from the server and/or client connections. In some cases, this can leak sensitive data such as clear-text credentials.
Severity: CRITICAL | Exploit Available: Yes | Exploitability: Easy | Remotely Exploitable: Yes
Description
Apache Tomcat from 8.5.7 through 8.5.63, from 9.0.0-M11 through 9.0.43 are vulnerable to client-side de-sync attacks. For more info regarding Client-Side De-Sync attacks, please refer to James Kettle’s research here: Browser-Powered Desync Attacks: A New Frontier in HTTP Request Smuggling
Impact
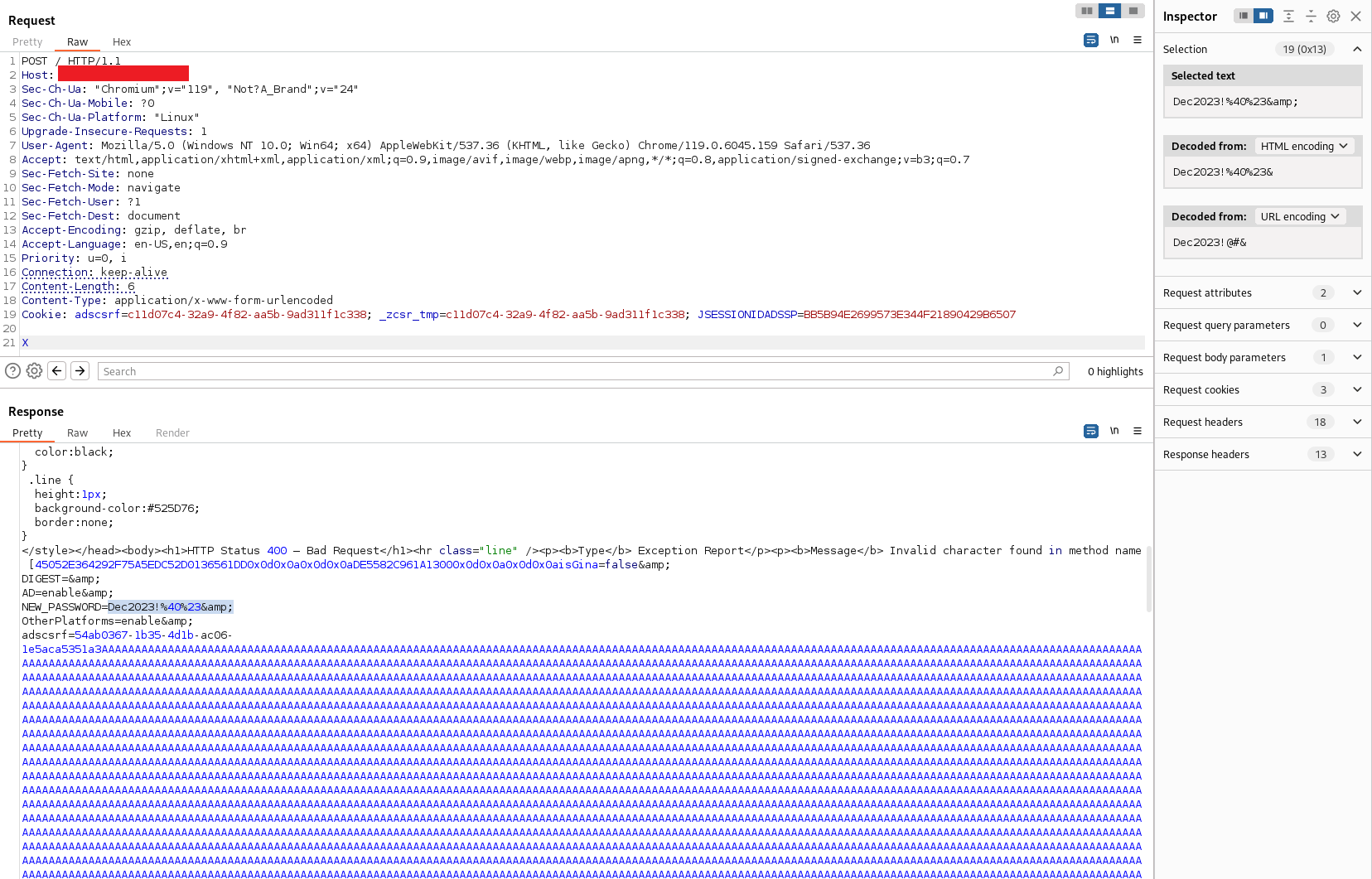
Vulnerabilities related to client-side de-synchronization (CSD) arise when a web server fails to accurately process the Content-Length of POST requests. Exploiting this issue enables an attacker to manipulate a victim’s browser, leading to a disconnection misalignment with the website. This manipulation can result in the unauthorized extraction of sensitive data from both server and client connections.
The severity of the impact varies based on the applications utilizing Tomcat as the backend web server, potentially exposing confidential information such as clear-text credentials. For instance, our team identified an instance in ManageEngine’s ADSelfService Plus portal prior to version 6304, where clear-text Active Directory credentials could be surreptitiously obtained from client connections as seen below.
For a full list of affected ManageEngine products and versions, please see https://www.manageengine.com/security/advisory/tomcat/Advisory-CVE-2024-21733.html for more details. Given the severity of this vulnerability, ManageEngine customers are strongly advised to upgrade to the latest build of the affected products immediately.
PoC / Exploit
Affected Software
Apache Tomcat from 8.5.7 through 8.5.63, from 9.0.0-M11 through 9.0.43 are vulnerable.
Product Description
The Apache Tomcat® software is an open source implementation of the Jakarta Servlet, Jakarta Server Pages, Jakarta Expression Language, Jakarta WebSocket, Jakarta Annotations and Jakarta Authentication specifications.
Solution
Users are recommended to upgrade to version 8.5.64 onwards or 9.0.44 onwards, which contain a fix for the issue.
Detection
A template to detect this vulnerability will be made available exclusively to Sn1per Professional and Sn1per Enterprise customers within 30 days of the patch being released.
References
https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2024-21733
https://tomcat.apache.org/security-9.html
https://tomcat.apache.org/security-8.html
https://portswigger.net/research/browser-powered-desync-attacks
Credit
xer0dayz from Sn1perSecurity LLC