Passive Reconnaissance Techniques For Penetration Testing
As a top ranked bug bounty researcher and Sr. Penetration Tester, I’ve discovered some critical vulnerabilities without ever directly accessing or scanning the target in question. These vulnerabilities are typically found by querying 3rd party services to discover cached and historic URL’s from a target and searching interesting URL’s. In some cases, this has lead me to discover critical “0day” vulnerabilities in commercial security products, Corporate owned websites and online services. In this blog post, I’ll discuss the methodology and step-by-step process used to find these vulnerabilities and how we can leverage tools like Sn1per Professional to assist us.
Passive Reconnaissance
We tend to glorify complex security issues, but more often than not, it’s the simple things that can have an even greater impact to a target’s privacy and security. It’s also easy to fall in to the trap of thinking that we have to scan everything to find impactful bugs, but that’s not always the case. What if we could query a target passively and take over accounts or services without ever touching the target directly? With some passive reconnaissance skills, and a little luck, we should have no problems doing just that.
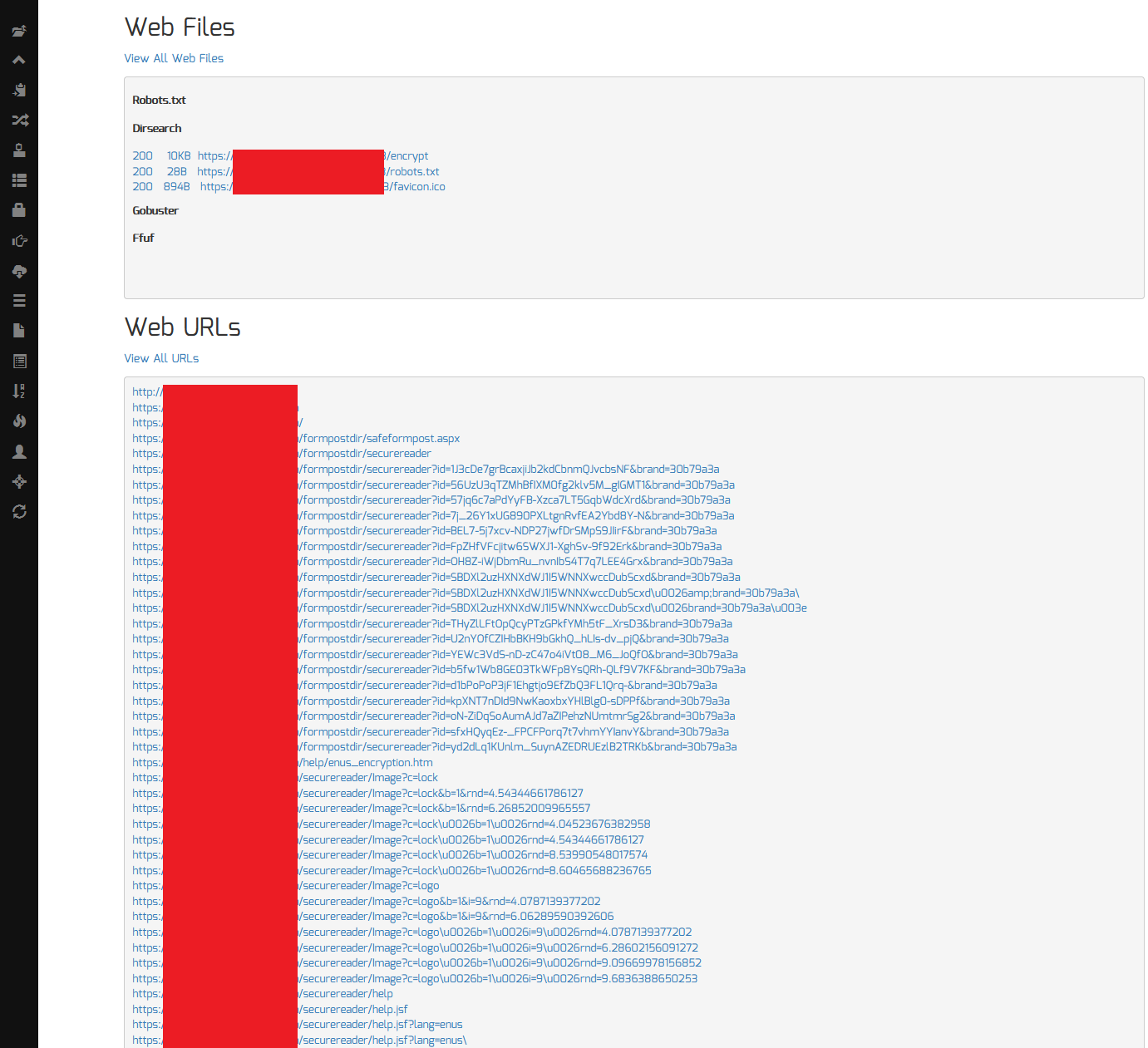
To start, we can perform passive reconnaissance using Sn1per as a starting point. Since Sn1per already integrates many 3rd party API’s to passively gather all URL’s, a simple ‘stealth‘ mode scan (ie. sniper -t target.tld -m stealth -w target.tld) of the target TLD (Top Level Domain) will usually suffice. Once the scan is complete, we can then view all URL’s from the Sn1per Professional web UI or command line output to look for interesting URL’s.
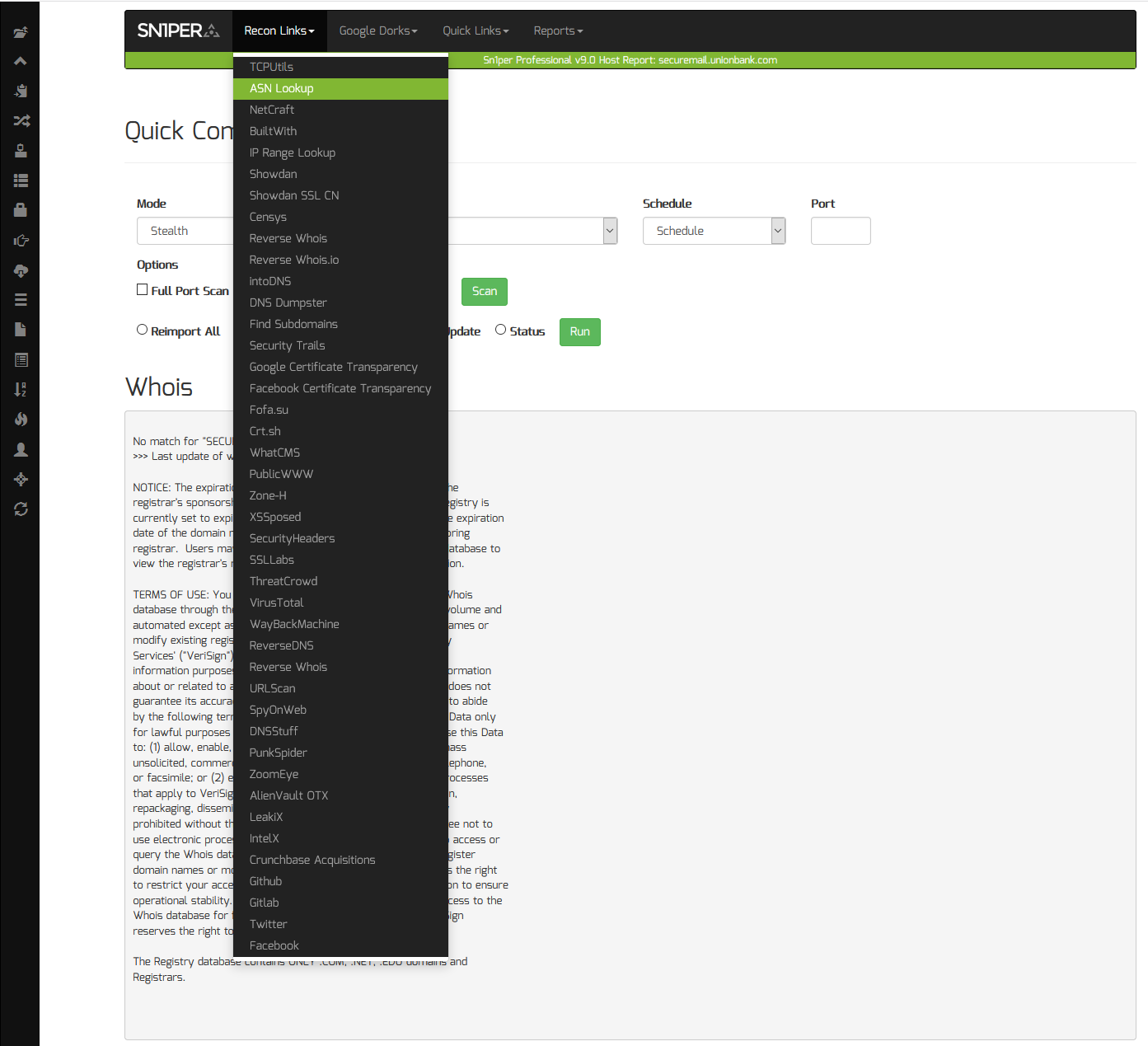
We can also leverage Sn1per Professional‘s built-in “Recon Links” and “Google Dorks” lists to assist us in finding interesting URL’s by selecting any of the built-in links available from the web UI. This can be used to search for sub-domains using online services such as Security Trails or DNS Dumpster or gather URL’s on a target using services such as URLScan.io, PublicWWW or SpyOnWeb.
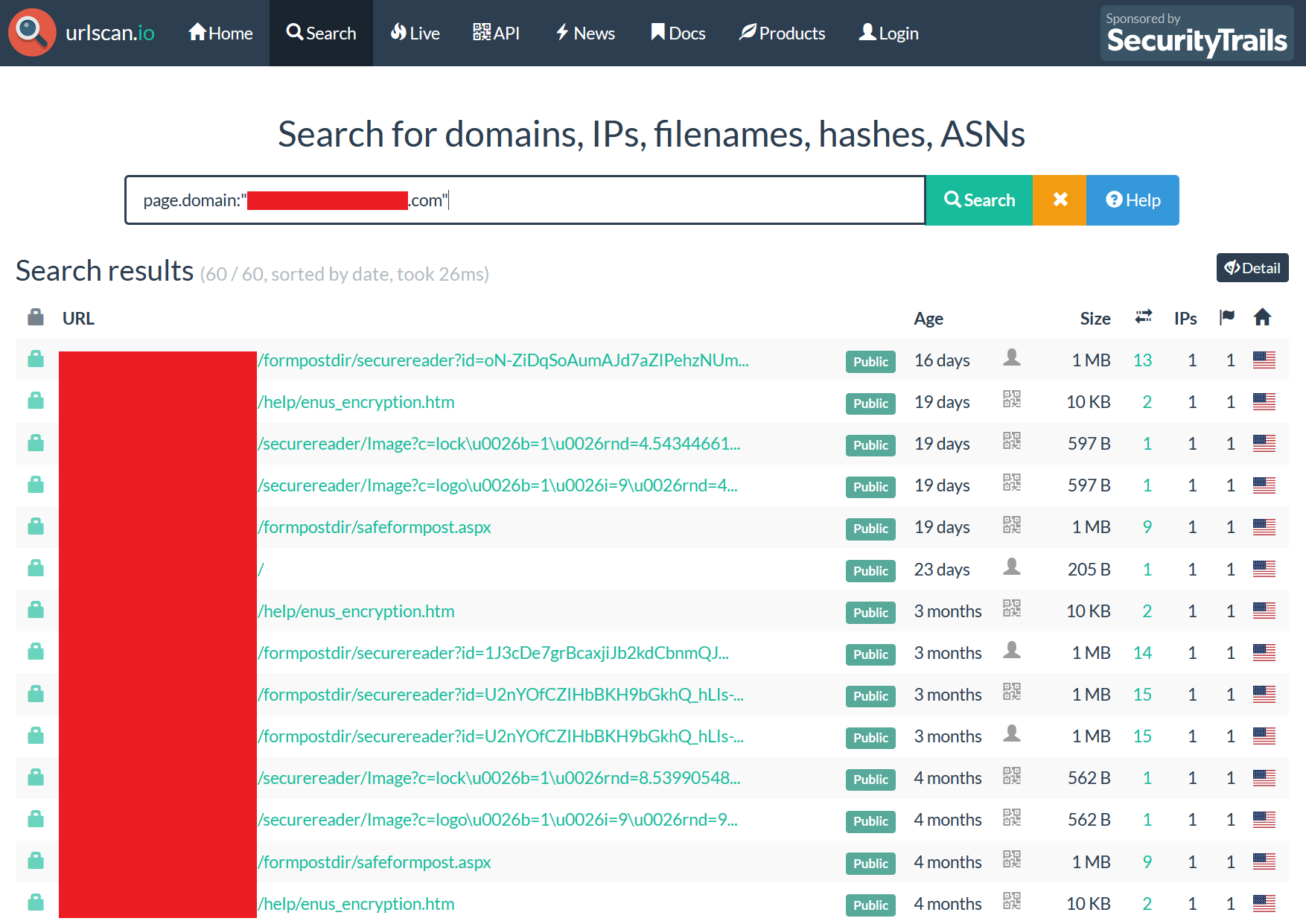
The below screenshot shows the result after selecting URLScan as an example.
Finding Interesting URL’s
With some time and experience either pentesting or bug bounty hunting, finding “interesting” URL’s will become a natural skill. In the meantime though, looking for strings such as “token“, “activation“, “password“, “reset” or “id“, etc. in the URL is usually a good start. If we know the the URL scheme being used for sensitive functions such as account activation or password reset links, we can specifically search for the affected URL’s using our online recon or Google dork links to see if any have been cached online.
In some cases, this could yield some interesting vulnerabilities, such as:
- Un-used account activation or password reset links
- Sensitive information disclosed in the URL (ie. usernames, passwords, tokens, etc.)
- Sensitive or cached information disclosed in the response (email addresses, first and last name, etc.)
After we gather all URL’s, we can use a 3rd party “URL to screenshot” service such as http://www.urltoscreenshot.com/ to passively view the URLs without ever touching the target site ourselves (if we’re concerned about disclosing our IP address). Otherwise, we can click on the links manually from the web UI to view them in a web browser for easy viewing.
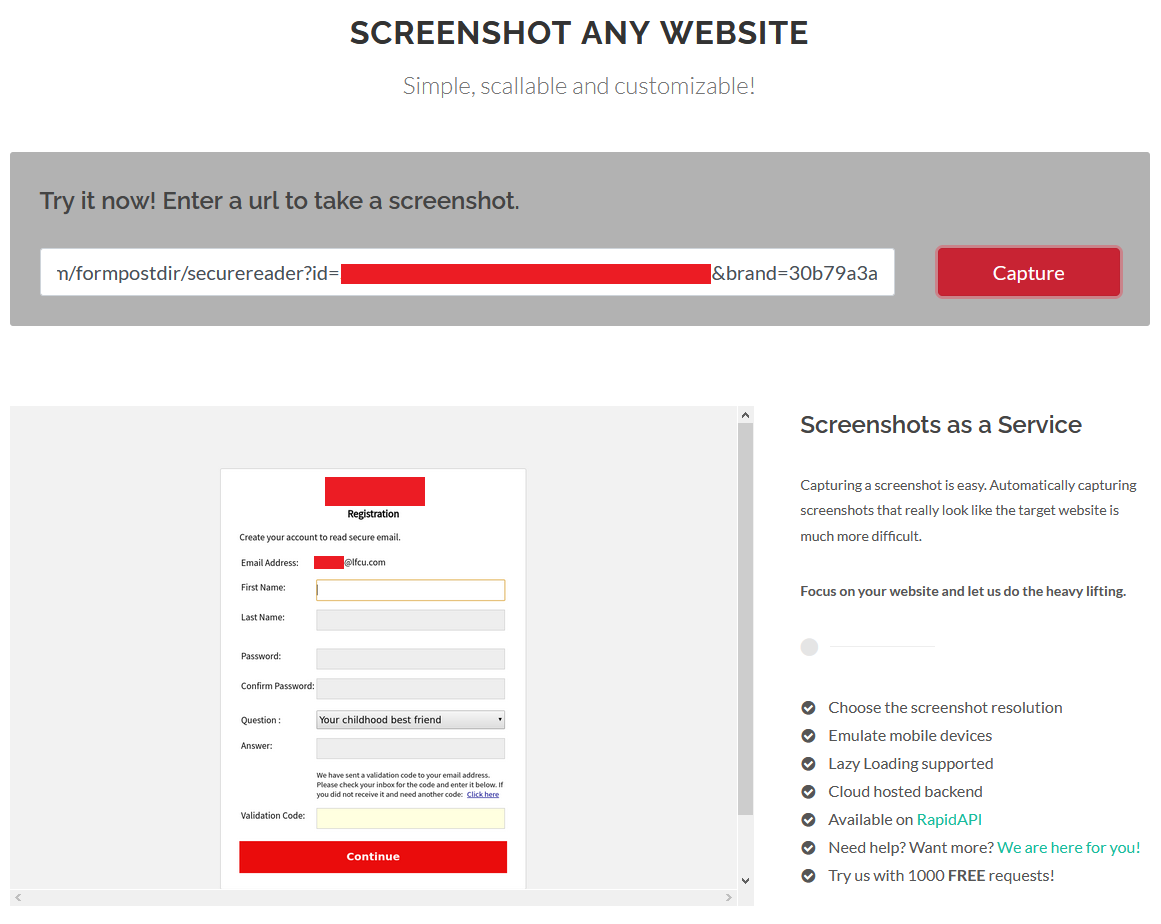
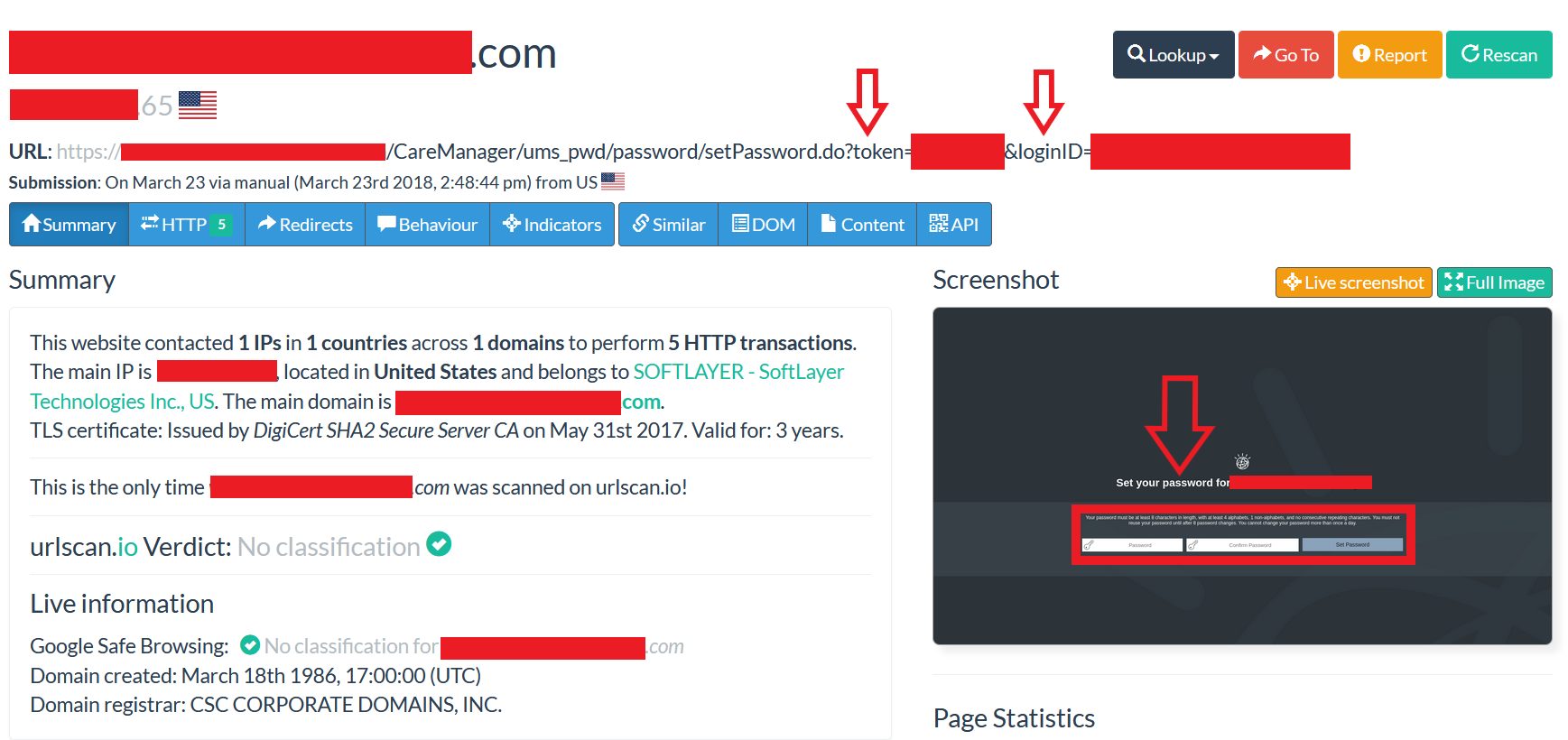
Account Takeover via Activation and Password Reset Links
The screenshot below shows an example of these types of vulnerabilities where the account activation token or ID is sent via the URL. If an attacker obtains this link before the user activates their account, the attacker can takeover accounts on the vulnerable service by setting a password and any other security questions presented. Some services may also reveal the customers email address or personal information such as first and last name or more just by accessing the affected URL as seen below.
Account Takeover via Sensitive Information Leaked in the URL
In other scenarios, the password reset or account activation tokens, usernames and clear-text passwords may be disclosed in the URL (seen below) which could allow external attackers to take over the affected account(s). The possibilities are endless, but as you can see, just by collecting and analyzing interesting URL’s, we can find some pretty impactful vulnerabilities.
Depending on the service in question, this can lead to compromised accounts which provide critical functions such as encrypted email or privileged access to back-end systems and data.
Final Thoughts
These are just a few examples of passive attacks that can be performed without ever touching a target’s perimeter. The impact of these attacks can result in complete account takeover and compromise to leaking sensitive information publicly. Tools such as Sn1per Professional provide an easy-to-use workflow and access to many valuable services which can aid in this process.
As a general guide for protecting from these types of attacks:
- Sensitive information should never be present in the URL as it can be cached and stored and potentially accessed by unauthorized individuals.
- Account activation and password reset tokens should be expired after a reasonable time frame (ie. a few days to a week) and should be expired immediately after use to reduce the likelihood of attack.
- Sensitive data such as usernames, passwords or re-usable tokens should be submitted using the HTTP POST method to avoid sensitive data being transmitted via the URL.