Sn1per Scan Engine v10.3 Released!
New Vulnerability Templates
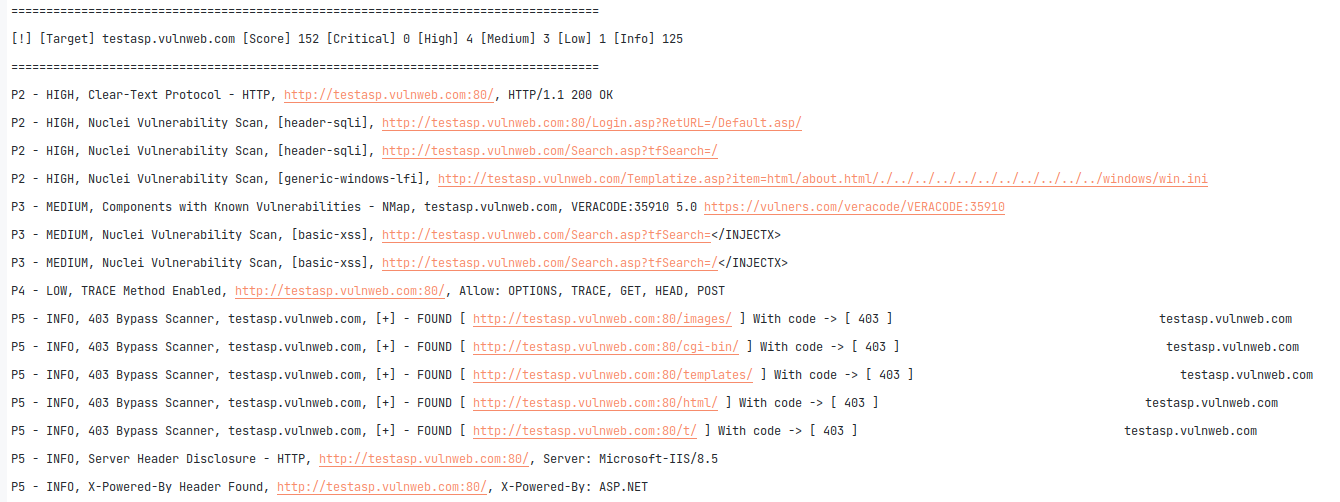
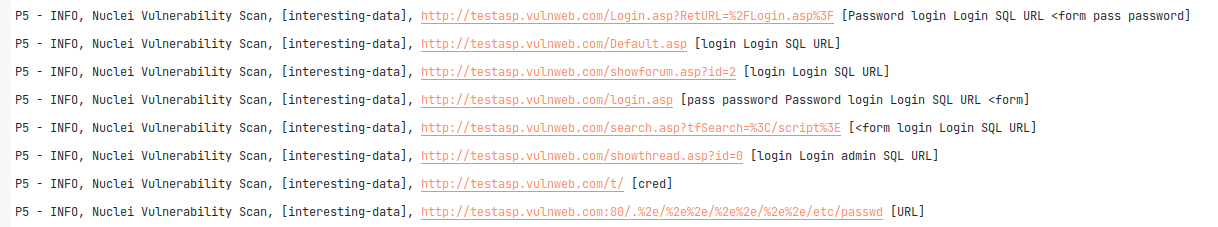
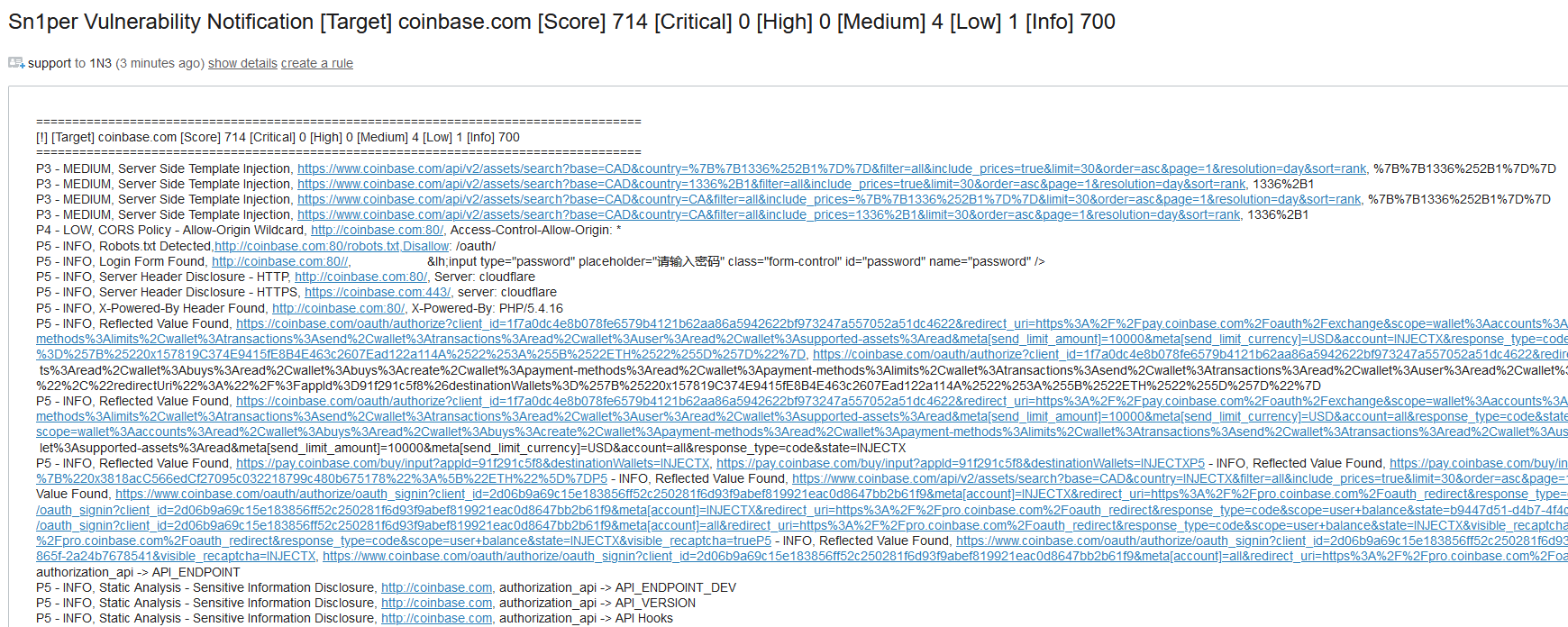
46 custom/private OWASP fuzzer templates were added in Sn1per v10.3 to dynamically fuzz all URL’s or SQLi, XSS, RCE, etc. This has added a ton of new scanning capabilities for improved vulnerability detection. 2 new custom static templates were also added detect sensitive and interesting data across all URL’s discovered as well, giving customers an advantage at finding more interesting vulnerabilities and disclosures.
- Scan for web server vulnerabilities
- Scan all dynamic URL’s for OWASP vulnerabilities (ie. SQLi, XSS, Traversal, etc.)
- Statically scan all URL’s discovered for interesting and sensitive data
- Statically scan all JavaScript URL’s for DOM XSS and sensitive data
This will vastly improve Sn1per’s ability to detect dynamic vulnerabilities such as Cross-Site Scripting (XSS), SQL injection, etc. across all URLs discovered.
New Features
SMTP integration and email notifications were added to Sn1per v10.3. Similar to Sn1per’s current Slack integration, SMTP notifications will allow customers to set their SMTP server and notification preferences to receive a full text-based notification when certain events are triggered. The event types are list below for reference:
- New domains
- New sub-domain takeovers
- New vulnerabilities
To setup SMTP notifications, a valid SMTP server will already need to be established and working and the following will need to be set in either your Sn1per configuration file or /root/.sniper_api_keys.conf:
##-------------------------------------------------------## SMTP SETTINGS SMTP_ALERTS_EMAIL_FROM="[email protected]" SMTP_ALERTS_EMAIL_TO="[email protected]" SMTP_ALERTS_NEW_DOMAINS="1" SMTP_ALERTS_TAKEOVERS="1" SMTP_ALERTS_VULNERABILITIES="1" # ONLY ALERTS ON > INFO VULNS
Hidden web content discovery was also greatly enhanced in Sn1per v10.3 with the use of FFuF and a new and improved (private/custom) wordlist, yielding faster, more accurate results.
A new tool named “RequestX” (private) was added to validate all URL’s discovered, and “uro” was added to reduce the number of URL’s and only show unique endpoints. Wget was also added to replace BlackWidow for active web spidering.
Fixes
A number of new fixes were also added to Sn1per v10.3 to ensure comparability with the latest tools and releases. These include updates to OpenVAS/GVM, Burpsuite Professional and Nuclei to name a few.
For a full change log, please see below.
Changelog
# NEW TEMPLATES
* v10.3 – Added 46 custom/private OWASP fuzzer templates for Nuclei to dynamically fuzz for SQLi, XSS, RCE, etc.
* v10.3 – Added 2 custom/private static Nuclei templates to detect sensitive and interesting data
* v10.3 – Added Apache Spark UI – Command Injection – CVE-2022-33891
* v10.3 – Added Salesforce Login Portal detection
* v10.3 – Added sc0pe template for Forbidden 403 bypass confirmation
# NEW FEATURES
* v10.3 – Added SMTP/email notifications and alerts
* v10.3 – Added Nuclei dynamic URL fuzzer to replace InjectX tool using custom/private templates
* v10.3 – Added Nuclei static URL scanner for interesting/sensitive data using custom/private templates
* v10.3 – Added auto Nuclei AI network scan when non-web ports are found
* v10.3 – Switched default hidden content discovery tool to FFuF
* v10.3 – Updated web brute force wordlist and options for improved accuracy and greater results
* v10.3 – Added new “combined-url” list to combine both validated URL’s and also hidden/discovered URL’s into a single file (urls-combined-$TARGET.txt)
* v10.3 – Updated default SSH NMap scripts to exclude brute forcing
* v10.3 – Added port 8009 AJP exploitation and NMap scripts
* v10.3 – Added new streamlined install script
# NEW TOOLS
* v10.2 – Added RequestX tool (credit: @xer0dayz) to validate URL’s
* v10.3 – Added uro tool https://github.com/s0md3v/uro
* v10.3 – Added wget spider function to replace BlackWidow tool
# FIXES
* v10.3 – Fixed issue with GVM socket integration issue
* v10.3 – Fixed xargs unneeded arguments
* v10.3 – Updated/added support for Burpsuite Pro 2022.9.5
* v10.3 – Updated Commoncrawl passive URL DB
Update Instructions
To update to Sn1per v10.3, customers can run the ‘sniper -u‘ command from the command line or use the ‘Update‘ function from the Command Execution module.