Sn1per Scan Engine v10.4 Released!
New Vulnerability Templates
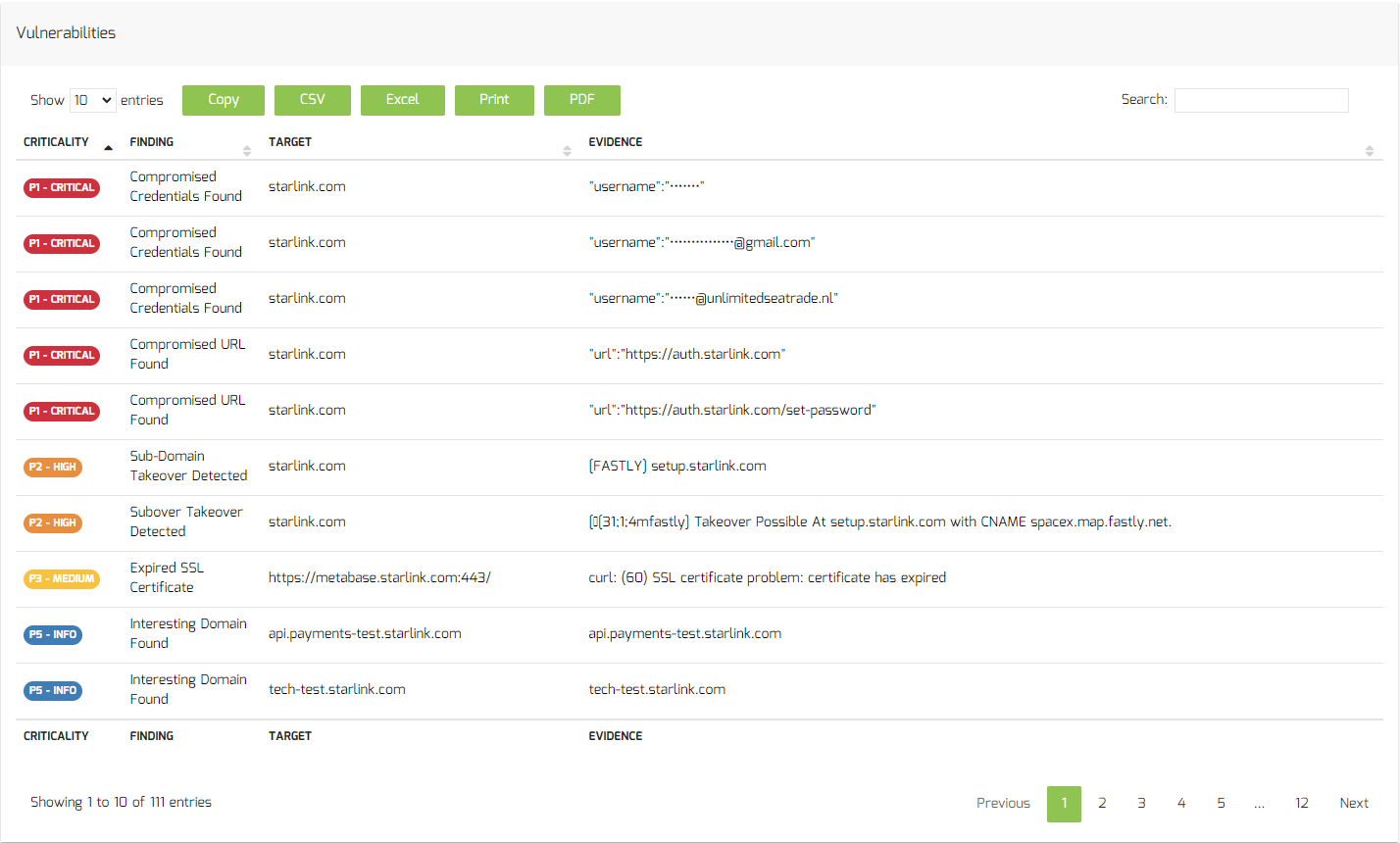
* v10.4 – Added HudsonRock compromised credentials and URL template (head over to https://www.hudsonrock.com/ for full API access)
* v10.4 – Added CVE-2023-23752 Joomla Improper AccessCheck in WebService Endpoint template
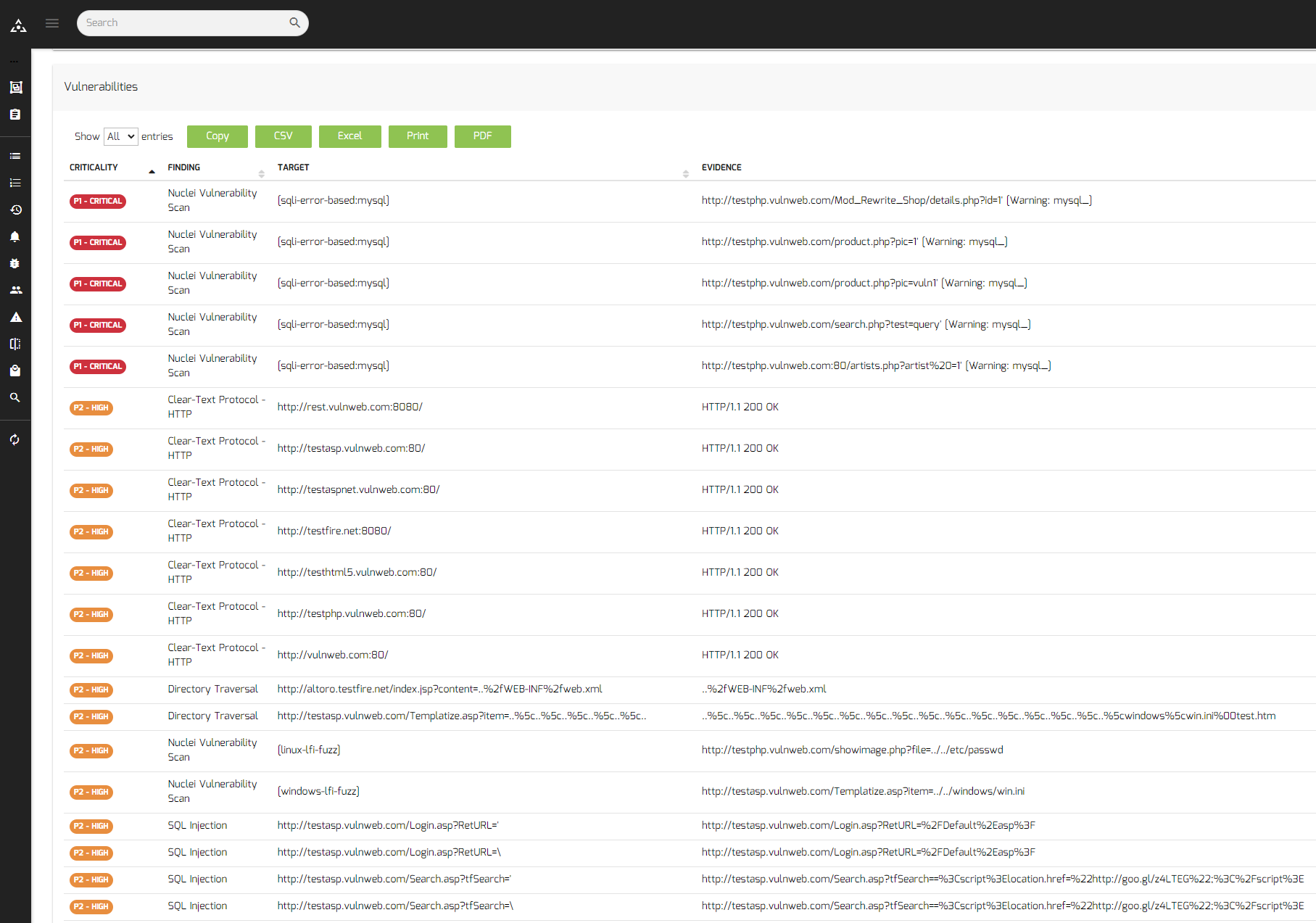
* v10.4 – Added official Nuclei fuzzing-templates repo to active web fuzzer
* v10.4 – Added InjectX fuzzer template to parse all vulnerabilities
New Features
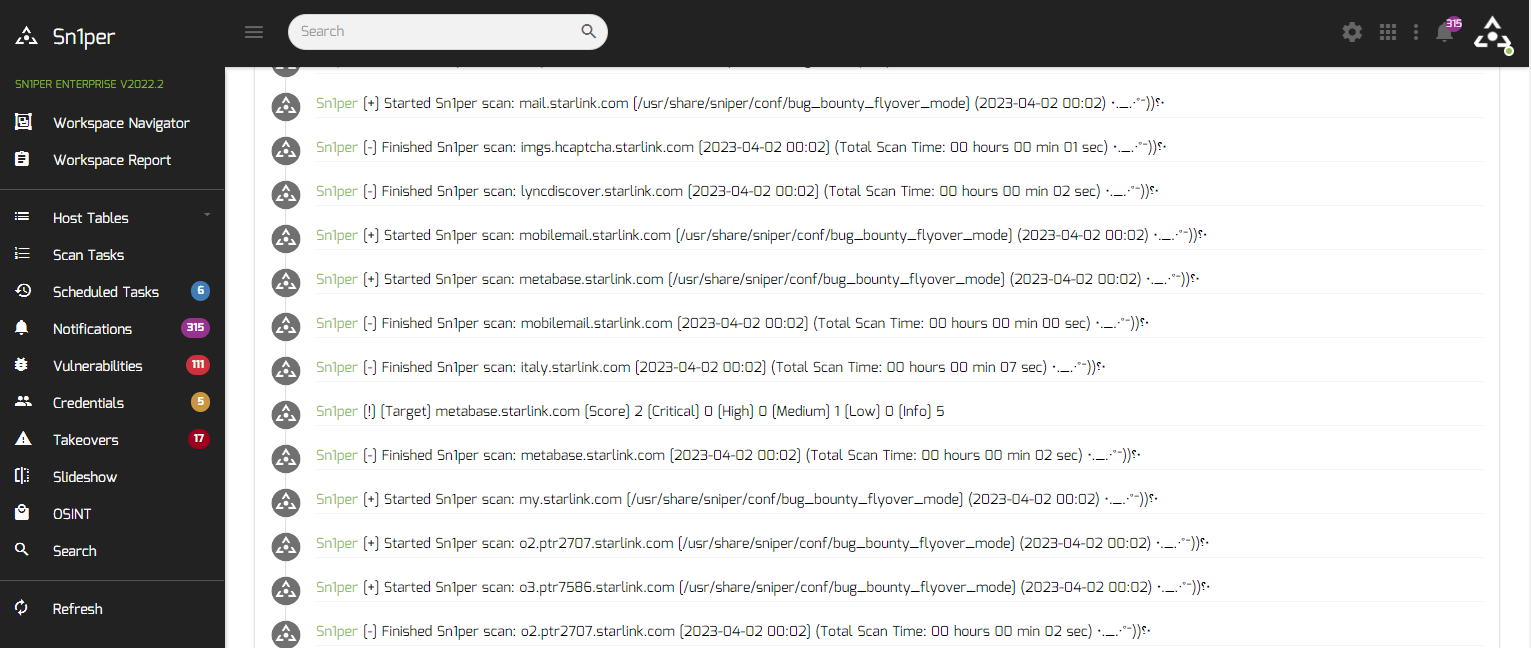
* v10.4 – Added per host config to allow multi-threaded scans to maintain unique configs
* v10.4 – Added total elapsed time to notifications for all scans
* v10.4 – Added automatic Nuclei network scans if non-web ports are opened
* v10.4 – Added scan logic to only scan port 443 using stealth mode if WAF is detected to avoid getting blocked
* v10.4 – Added running config to scan task viewer for all targets to view which conf was selected
* v10.4 – Added HudsonRock API integration for compromised credentials check (head over to https://www.hudsonrock.com/ for full API access)
* v10.4 – Added wildcard domain check to cancel recon scans if wildcard is detected
* v10.4 – Added new setting DOMAINS_MAX to set the maximum number of sub-domains to scan
* v10.4 – Added new setting VALIDATE_URLS_MAX to validate all discovered URLs
* v10.4 – Updated Docker build template
New Tools
* v10.4 – Added updated impacket tools (ie. samrdump, etc.)
Fixes
* v10.4 – Removed h8mail tool
* v10.4 – Remove Inurlbr tool
* v10.4 – Removed Slurp tool
* v10.4 – Removed AMap tool from conf
* v10.4 – Fixed bad Subover providers list link
Update Instructions
To update to Sn1per v10.4, customers can run the ‘sniper -u‘ command from the command line or use the ‘Update‘ function from the Command Execution module.