Spring4Shell (CVE-2022-22965) Detection with Sn1per Professional
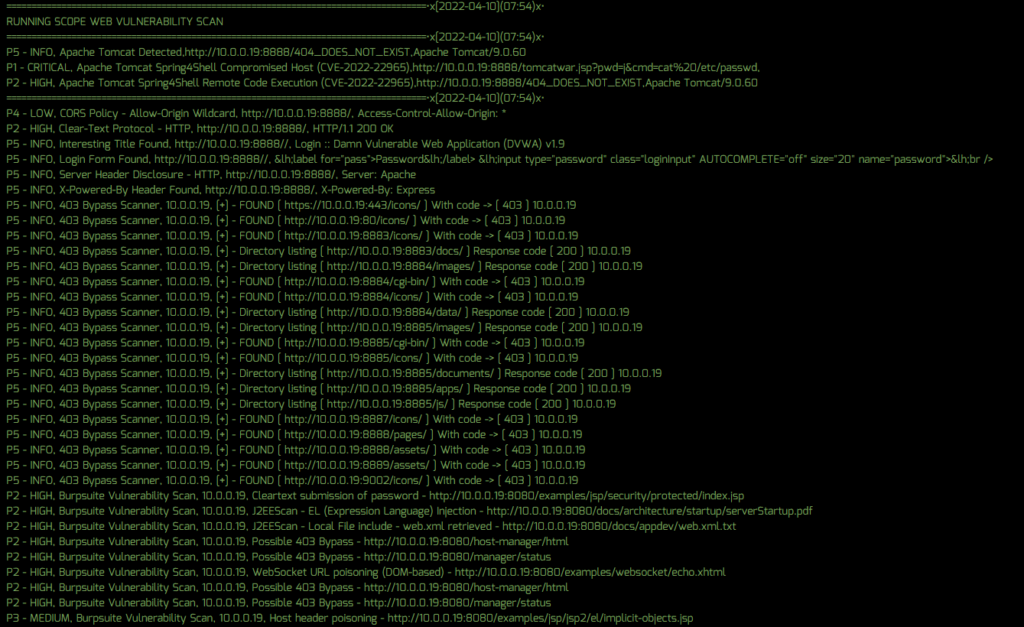
On March 30, 2022, information regarding a critical 0-day vulnerability affecting the Spring Framework was disclosed and dubbed “Spring4Shell” CVE-2022-22965 which allows an un-authenticated attacker to execute arbitrary code on vulnerable servers. Given the impact and severity of the vulnerability, Sn1perSecurity has released an out-of-band update to help detect vulnerable and compromised servers in your environment using Sn1per Professional. This update also includes improved detection for Apache Tomcat which is required in order to exploit this vulnerability.
Severity: CRITICAL | Exploit Available: Yes | Exploitability: Easy | Remotely Exploitable: Yes
Scanning for Spring4Shell (CVE-2022-22965)
To detect the Spring4Shell vulnerability using Sn1per Professional, you will need to do the following:
- Apply the template update from the Sn1per Professional “Updates” panel
- Ensure that the “SC0PE_VULNERABLITY_SCANNER” is set to “1” in your Sn1per configuration
- Run a scan of your network using the normal Sn1per scan process
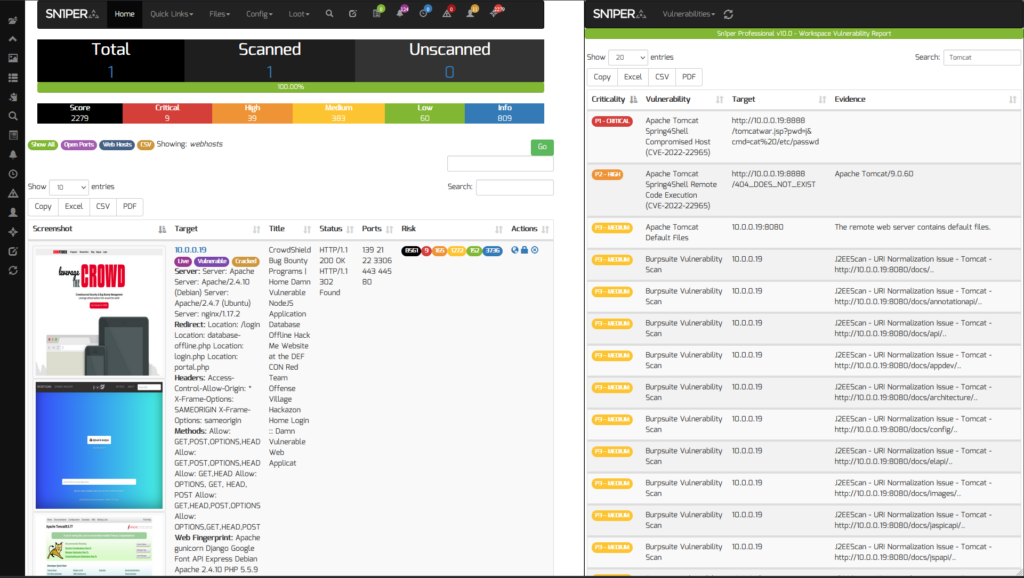
After the scan finishes, you can then view all vulnerable instances from the Sn1per Professional “Vulnerability Report Viewer“.