Sn1per Scan Engine v10.2 Released!
New Vulnerability Templates
Several new critical vulnerability templates were added in v10.2 to detect the latest CVE’s and vulnerabilities in your environment.
- Added Confluence Remote Code Execution via OGNL template injection CVE-2022-26134 sc0pe template
- Added F5 BIG-IP iControl REST Auth Bypass RCE – CVE-2022-1388 sc0pe template
- Added VMware vCenter Unauthenticated Arbitrary File Read sc0pe template
- Added Ubuntu Landscape Portal Found sc0pe template
- Added Splunk Enterprise Portal Detected sc0pe template
- Updated PHP Info Disclosure sc0pe templates to fix F+ results
New Tools
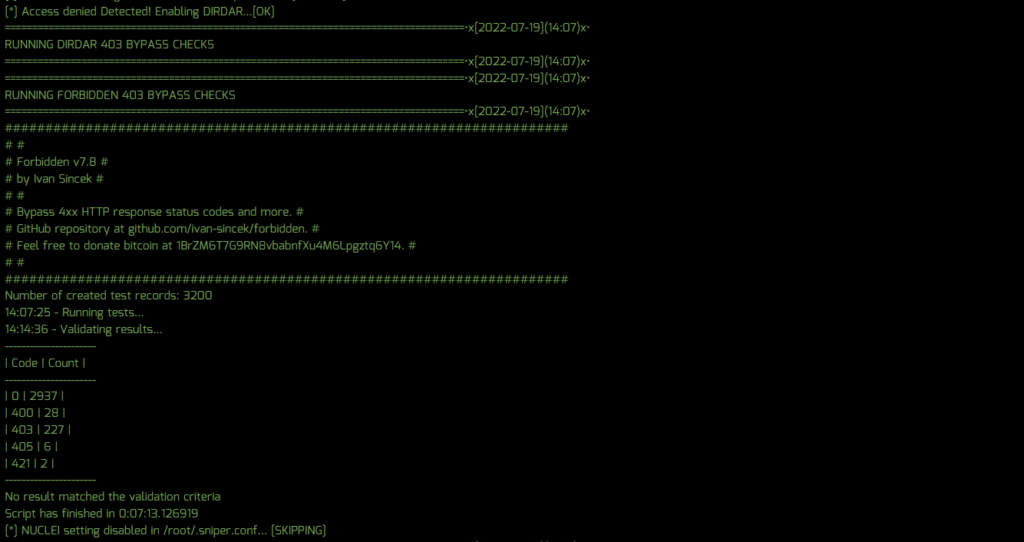
Three new tools were added to Sn1per, including Forbidden which checks for 403 bypasses, a new web crawler via Wget, and custom multi-threaded DNS resolver via Dig.
- Added Forbidden 403 tool to check for bypasses (AI activated by default when 403 status found)
- Added new Wget spider/web crawler to collect URL’s (WGET setting added – enabled by default)
- Added new dig multi-threaded resolver to recon mode (DIG_MASS_RESOLVE setting added – enabled by default)
New Features
Customers using Sn1per SE 10.2 will now retrieve Sn1per, Nuclei and WPScan updates automatically by running the ‘sniper -u’ command to ensure the latest vulnerabilities are detected (This can also be ran from the web UI ‘update’ function). We also added new lists for dynamic parameters and web hosts with 200 status to make fuzzing these hosts/URL’s even easier and more efficient.
- Added automatic Nuclei template update script via ‘sniper -u’ command
- Added automatic WPScan update script via ‘sniper -u’ command
- Added AI setting for HTTP 403 forbidden found to automatically run DirDar and Forbidden bypass checks
- Added $LOOT_DIR/web/dynamic-params-$TARGET.txt file with list of dynamic parameters
- Added $LOOT_DIR/web/dynamic-unique-$TARGET.txt file with list of all dynamic URL’s
- Added new $LOOT_DIR/web/webhosts-200-status-sorted.txt list of web hosts with HTTP 200 status code
- Added new vulnerability alerting/notification for both Slack and UI notifications when severity of Low or greater is found
- Added MX DNS retrieval to OSINT mode
- Added weburls-sorted.txt list to /web/ directory for full web URL/host lists
- Added default Redis port 6379/tcp to all confs
New Settings
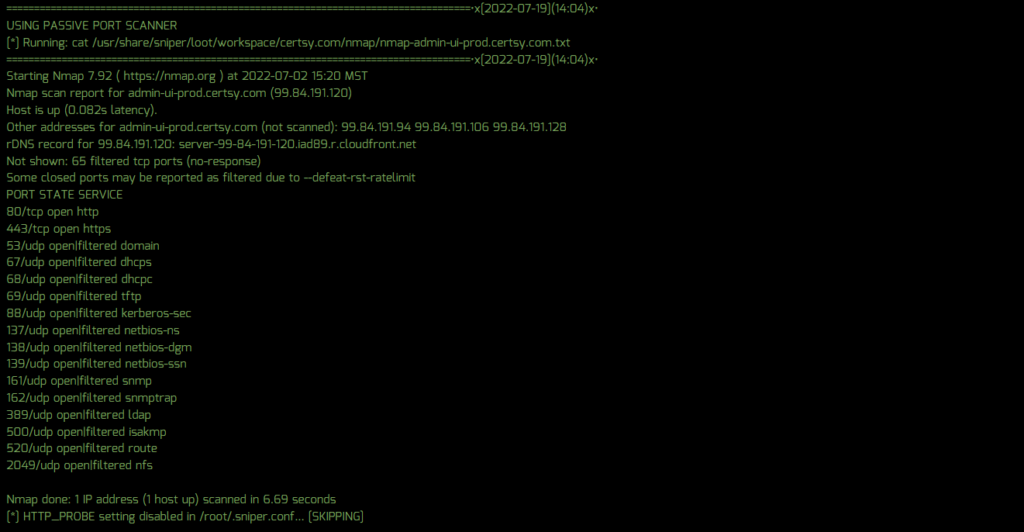
A number of new Sn1per configuration settings were added to further enhance scanning and alerting functionality. Notably, a PASSIVE_PORT_SCAN setting can be enabled to use existing NMap scan data to conduct future Sn1per scans for a vast performance increase and passive scan footprint. In addition, customers can now set the NUCLEI_TEMPLATES and NUCLEI_SEVERITY settings in their sniper.conf to set custom Nuclei template directories and files, along with the severity (ie. critical, high, medium, low, etc.) to scan for. These customizations can improve scan performance greatly while offering greater control over which vulnerabilities you want to scan for.
- Added PASSIVE_PORT_SCAN setting to conf to use existing port data to run scans – enabled by default
- Added NUCLEI_TEMPLATES and NUCLEI_SEVERITY settings to set custom Nuclei template locations and severity filters
- Added NUCLEI_NETWORK_SCAN setting to scan network ports/hosts for vulnerabilities – disabled by default
- Added SLACK_NOTIFICATIONS_VULNERABILITIES setting to alert on any low, medium, high and critical vulnerabilities
- Added SLACK_SCREENSHOTS setting to display web screenshots via Slack notifications
- Added SLACK_NOTIFICATIONS_SPIDER_NEW setting with URL totals to alert on new URL’s found
- Added SLACK_NOTIFICATIONS_DOMAINS_NEW setting to alert on new sub-domains found
- Added SCAN_ALL_RESOLVABLE_DOMAINS setting to automatically scan all resolvable domains found
- Added SCAN_NEW_DOMAINS setting to automatically scan new sub-domains found
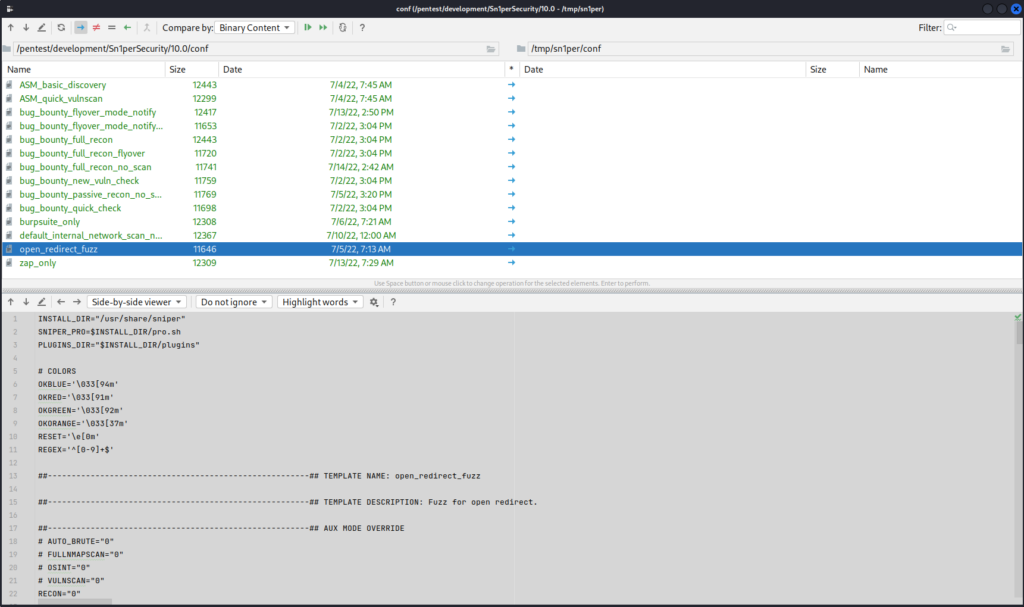
New Sn1per Configuration Templates
14 new Sn1per configuration templates were also added in v10.2 to the /sniper/conf directory to provide customers with various customizations that can be leveraged as part of their workflows and customized to meet their needs.
Fixes
- Fixed issue with Censys not working in latest version
- Fixed issue with Gobuster not working in latest version
- Fixed issue with Subfinder not working in latest version
- Fixed issue with Sublist3r command not working in latest version
Update Instructions
To update to Sn1per Scan Engine v10.2, customers can run the ‘sniper -u‘ command from the command line or use the ‘Update‘ function from the Command Execution module.